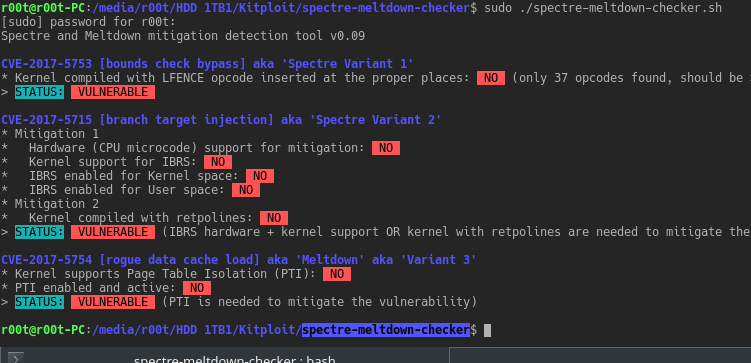
A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs: CVE-2017-5753 bounds check...
Search Results For - Vulnerability
It’s time to learn how to renew its OS because researcher James Bercegay has found a dozen models possess a hard-coded backdoor. The backdoor, lets anyone log...
A security researcher (@s1guza) has published the details of an unpatched vulnerability in macOS that can be exploited to gain full control of a system. The...
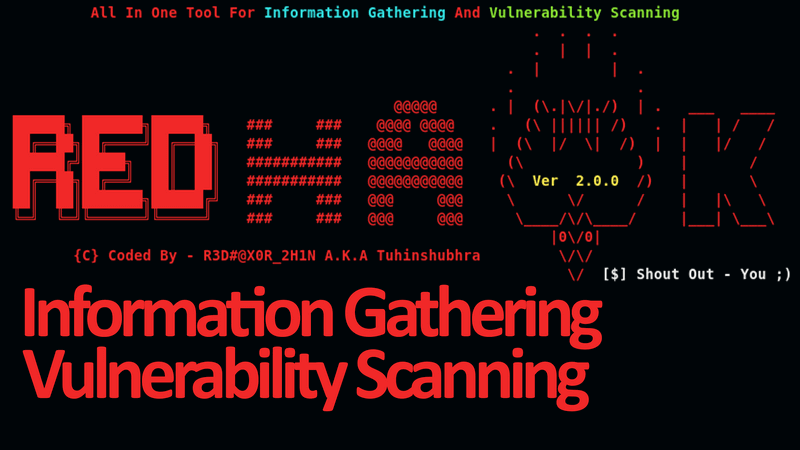
All in one tool for Information Gathering and Vulnerability Scanning RED HAWK : Scans That You Can Perform Using RED HAWK : Basic Scan Site Title NEW IP...
Archery is an opensource vulnerability assessment and management tool which helps developers and pentesters to perform scans and manage vulnerabilities...
XAttacker is a Website Vulnerability Scanner & Auto Exploiter developed by Mohamed Riahi Auto Cms Detect [1] WordPress : [+] Adblock Blocker [+] WP All...
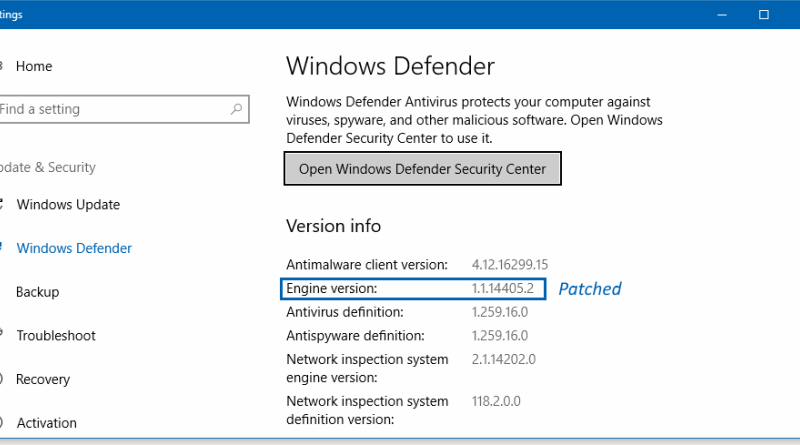
On Wednesday, Microsoft has released a patch for the Microsoft Malware Protection Engine (MPE) to fix a critical severity remote code execution (RCE) flaw in...
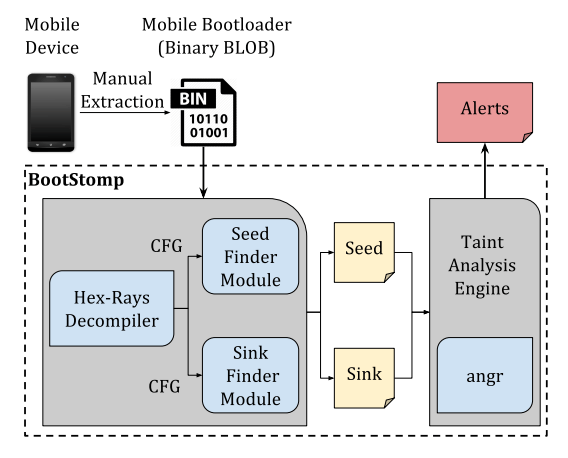
BootStomp is a boot-loader bug finder. It looks for two different class of bugs: memory corruption and state storage vulnerabilities. For more info please...
The flaw has been discovered by security researchers from the University of Birmingham, who tested hundreds of various banking applications and discovered that...
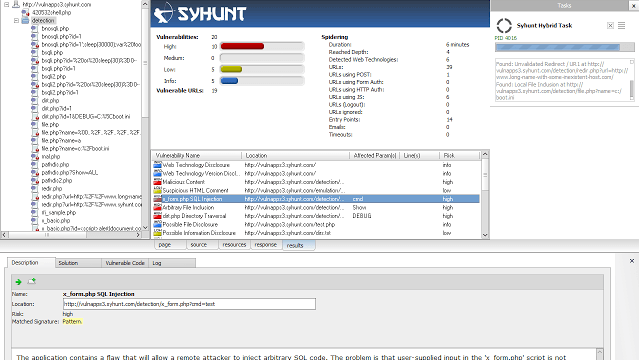
Syhunt ScanTools 6.0 adds advanced fingerprinting capabilities, enhanced spidering, injection and code scan capabilities, and a large number of improved checks...