Christmas is the time of the year where gift cards are on the rise. As per The National Retail Federation, people in the U.S are expected to spend $27.6...
Search Results For - Vulnerability
Last week, security researchers have published the details of two possibly critical flaws affecting version 5 of the vBulletin forum software. vBulletin is the...
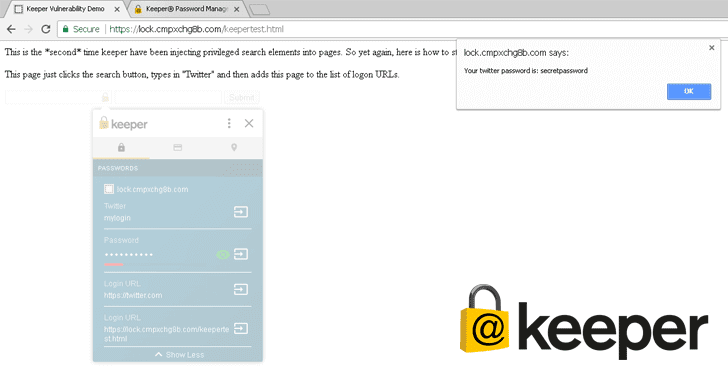
If you are running Windows 10 on your PC, then there are chances that your computer contains a pre-installed 3rd-party password manager app that lets attackers...
The security vulnerability was discovered in the Linksys WVBR0-25 wireless video bridge, which was designed to enable the main Genie DVR to communicate over...
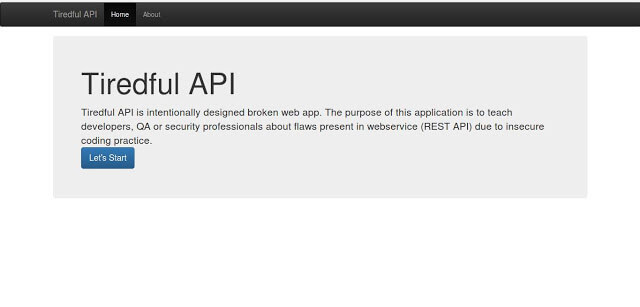
Tiredful API is intentionally designed broken app. The aim of this web app is to teach developers, QA or security professionals about flaws present in...
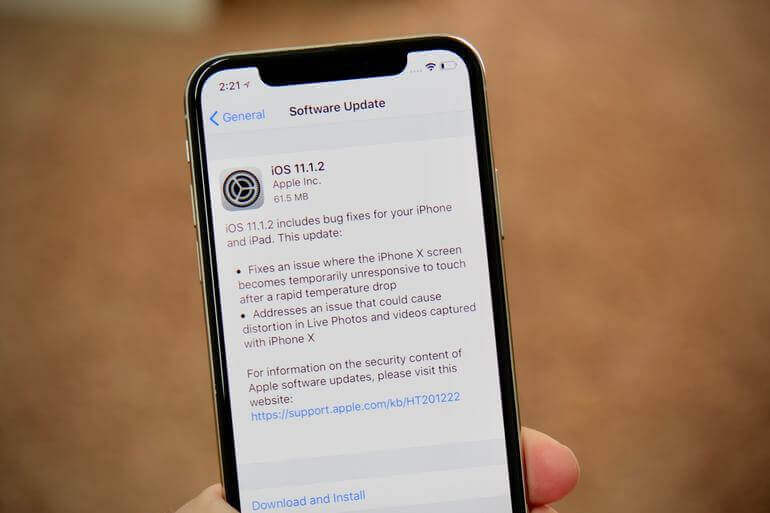
Google’s Project Zero iOS bug hunter Ian Beer has released details about an iOS 11 exploit that could offer up a jailbreak for iOS 11.1.2. Beer last week...
Palihapitiya’s judgments were directed not only at Facebook but the broader online ecosystem. “The short-term, dopamine-driven feedback circles we’ve produced...
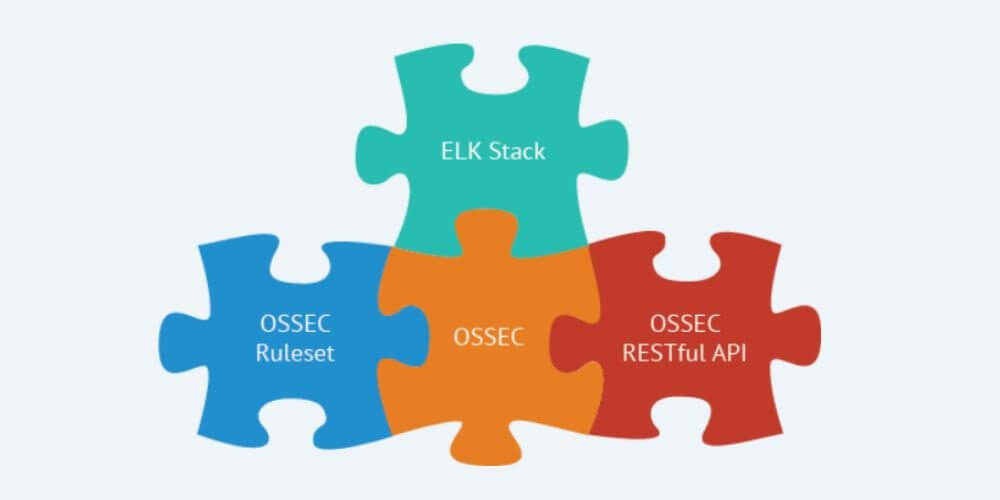
Wazuh is a security detection, visibility, and compliance open source project. It was born as a fork of OSSEC HIDS, later was integrated with Elastic Stack and...
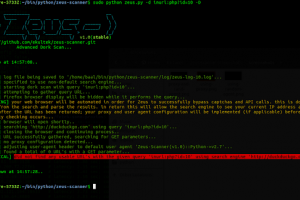
Zeus is an advanced reconnaissance utility designed to make web application reconnaissance simple. Zeus comes complete with a powerful built-in URL parsing...
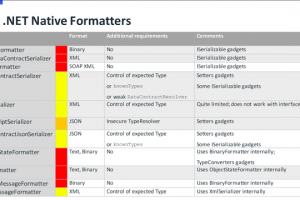
A proof-of-concept tool for generating payloads that exploit unsafe .NET object deserialization. Description ysoserial.net is a collection of utilities and...