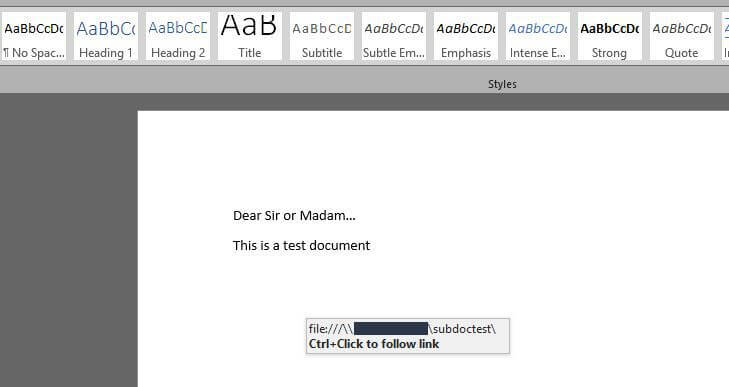
Security researchers from Rhino Labs (a US-based cyber-security firm) have found that cyber criminals can use a Microsoft Word feature dubbed subDoc to fool...
Search Results For - Vulnerability
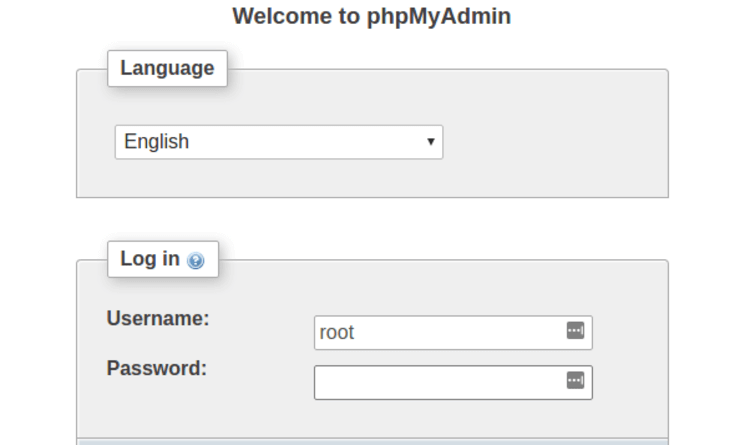
Amongst the most common and in demand applications for MySQL database management is the phpMyAdmin, which became vulnerable, when a critical flaw was found in...
Defeating Google’s audio reCaptcha system with 85% accuracy. Inspiration Across the Internet, hundreds of thousands of sites rely on Google’s...
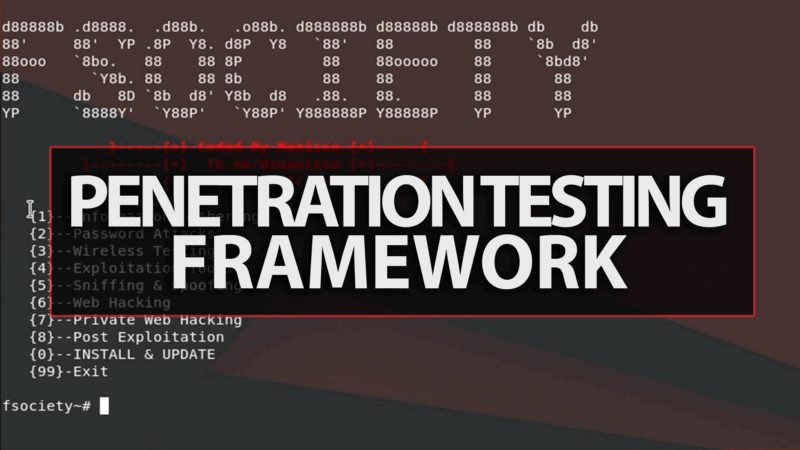
A Penetration Testing Framework, you will have every script that a hacker needs Fsociety: Menu Information Gathering Password Attacks Wireless Testing...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
Chiron is an IPv6 Security Assessment Framework, written in Python and employing Scapy. It is comprised of the following modules: • IPv6 Scanner • IPv6 Local...
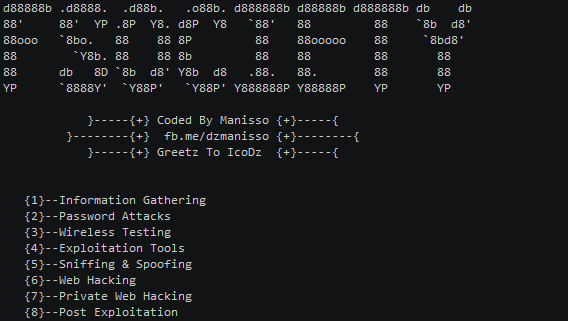
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
Russian ATMs Are Hackable It was recently revealed that some ATMs that are running in Russia are still operating on Windows XP operating system, which is why...
Security researchers from security firm Elttam have discovered a critical vulnerability (tracked as CVE-2017-17562) in GoAhead tiny web server that affects...
Windows 10 Facial Recognition System Is Hackable According to some experienced cyber security researchers, it was revealed that the facial recognition system...