Excalibur is an Eternalblue exploit based “Powershell” for the Bashbunny project. It’s purpose is to reflect on how a “simple”...
Search Results For - Vulnerability
Now security researchers have discovered that the camera can be silenced and frozen from a script run from any machine within Wi-Fi range, reports News. That...
Features Auto VoIP/UC penetration test Report generation Performance RFC compliant SIP TLS and IPv6 support SIP over websockets (and WSS) support (RFC 7118)...
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
Adobe’s latest security update has swatted a total of 67 bugs, some of them critical, in Adobe Flash, Acrobat, and Reader. On Tuesday, the software...
The Firefox sandboxing innovation confines the browser from the operating system in a way to block web attacks from using a vulnerability in the browser engine...
Security firm Positive Technologies lists being able to execute unsigned code on computers working the IME through USB. The fully fleshed-out details of the...
Device drivers are an essential part in modern Unix-like systems to handle operations on physical devices, from hard disks and printers to digital cameras and...
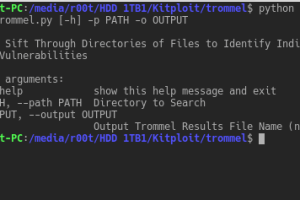
TROMMEL sifts through directories of files to identify indicators that may contain vulnerabilities. TROMMEL identifies the following indicators related to:...
Oracle Identity Manager (OIM) allows companies to manage the entire user life-cycle overall company resources both within and behind a firewall. Within Oracle...