Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in...
Search Results For - Virtual Machine
The goal of this volatility plugin is to extract a screenshot of all open X windows from a memory dump. Overview The plugin first dumps the X server memory...
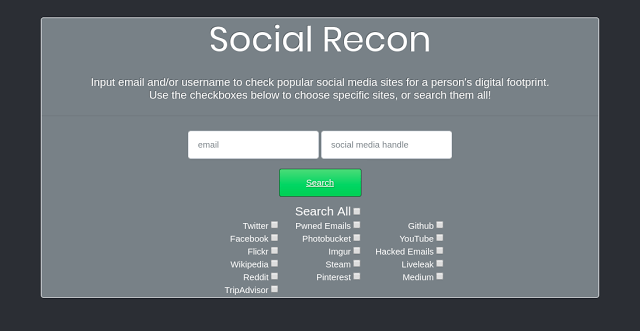
This application locates and compiles information about online personalities, given a username and/or email address. Use this to investigate your own online...
Collaborative (mitm) cryptocurrency mining pool in wifi networks. This script performs autonomous MITM attack on WiFi networks. It will inject a javascript in...
It’s time to learn how to renew its OS because researcher James Bercegay has found a dozen models possess a hard-coded backdoor. The backdoor, lets anyone log...
ratched is a Man-in-the-Middle (MitM) proxy that specifically intercepts TLS connections. It is intended to be used in conjunction with the Linux iptables...
Web Privacy Measurement is the observation of websites and serves to detect, characterize and quantify privacy-impacting behaviors. Applications of Web Privacy...
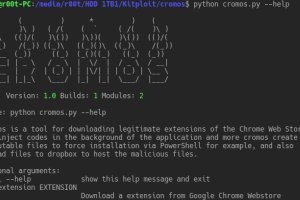
Cromos is a tool for downloading legitimate extensions of the Chrome Web Store and inject codes in the background of the application and more cromos create...
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...