Virtual Machine for Adversary Emulation and Threat Hunting RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by...
Search Results For - Virtual Machine
[sc name=”ad_1″] Vagrant VirtualBox Environment For Conducting An Internal Network Penetration Test. 1. Capsulecorp Pentest The Capsulecorp Pentest...
[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
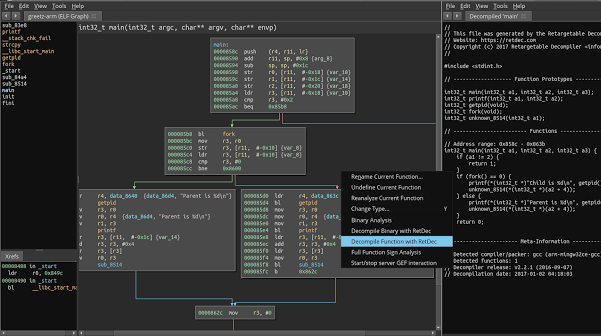
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
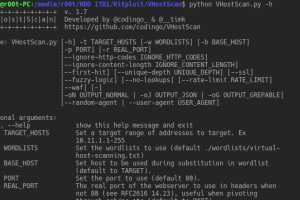
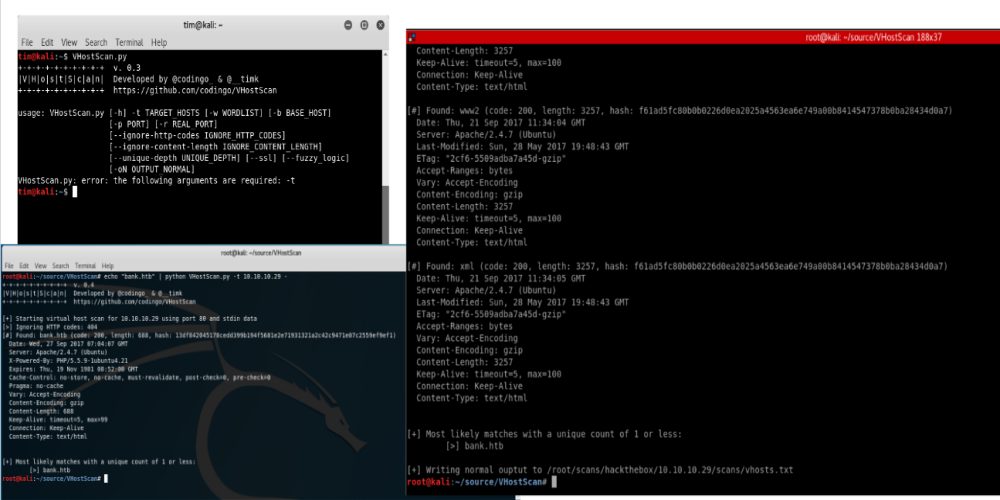
A virtual host scanner that can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages. First presented at SecTalks BNE in...
A virtual host scanner that can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages. First presented at SecTalks BNE in...
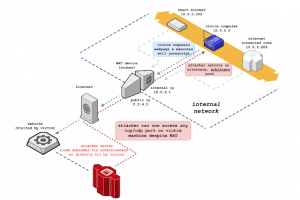
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
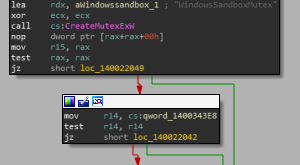
[sc name=”ad_1″] wsb-detect enables you to detect if you are running in Windows Sandbox (“WSB”). The sandbox is used by Windows...
[sc name=”ad_1″] Paradoxia Remote Access Tool. Features Paradoxia Console Feature Description Easy to use Paradoxia is extremely easy to use, So...
[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...