The Partnership sounds like something that would result on Facebook or Twitter, which are rife with imprinted content not on a site like Reddit. Well...
Search Results For - Twitter
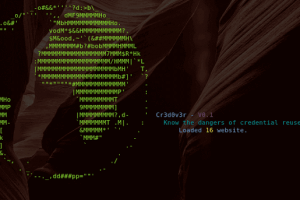
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
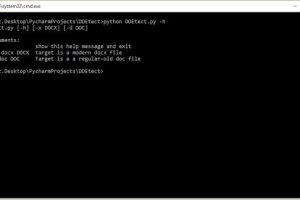
Written by Amit Serper, @0xAmit DDEtector is a simple DDE object detector written in python Currently supports only word DOCX and legacy DOC files Prints the...
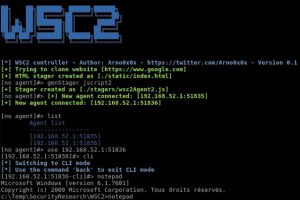
WSC2 is a PoC of using the WebSockets and a browser process to serve as a C2 communication channel between an agent, running on the target system, and a...
Kali Linux 2017.3 released, which includes all patches, fixes, updates, and improvements since our last release. In this release, the kernel has been updated...
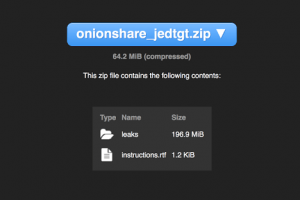
OnionShare lets you securely and anonymously share files of any size. It works by starting a web server, making it accessible as a Tor onion service, and...
SpookFlare has a different perspective to bypass security measures and it gives you the opportunity to bypass the endpoint countermeasures at the client-side...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...