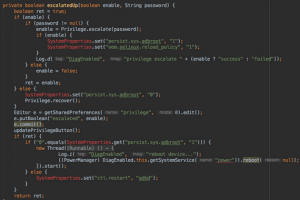
Just over a month after OnePlus was caught collecting personally identifiable information on its users, the Chinese smartphone company has been found leaving a...
Search Results For - Twitter
Faraday is the Integrated Multiuser Risk Environment you have always been looking for! It maps and leverages all the data you generate in real time, letting...
Bitcoin surged on Monday, recovering more than $1,000 after losing almost a third of its value in less than four days as traders bought back into the volatile...
News of the event was posted on Twitter by vigilante hacker, “The Jester,” who has in the past increased fame by hacking jihadist websites, and who in October...
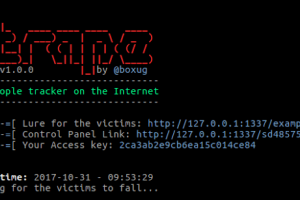
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
Wesley Neelen (security researcher) has received a phishing email that seems to be from the legal online Ethereum wallet site Myetherwallet.com. Cybercriminals...
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It...
A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack...
DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of...
The project is designed as a file resource cloner. Metadata, including digital signature, is extracted from one file and injected into another. Note: The...