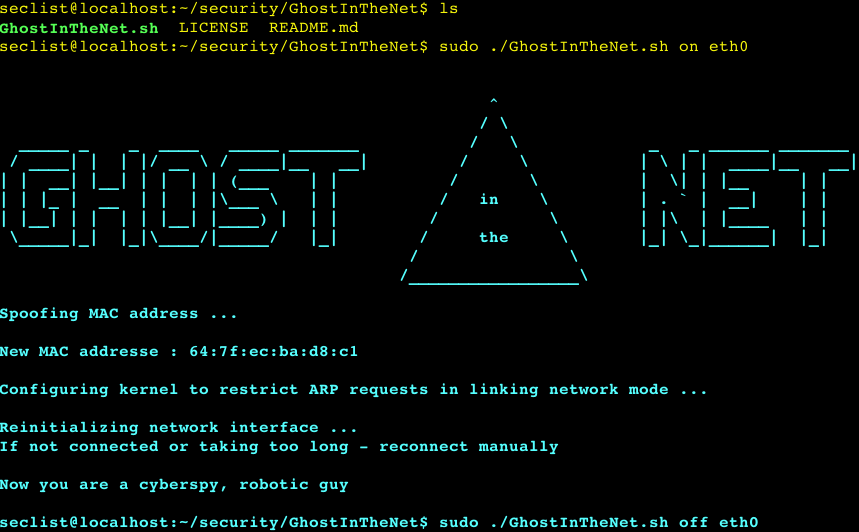
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
Search Results For - Stealth
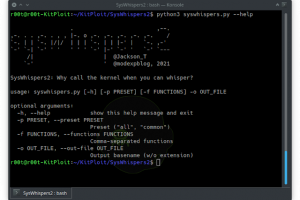
[sc name=”ad_1″] SysWhispers helps with evasion by generating header/ASM files implants can use to make direct system calls. All core syscalls are...
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
[sc name=”ad_1″] This is a tool that allows you to offensively use YARA to apply a filter to the events being reported by windows event logging...
[sc name=”ad_1″] HyperDbg is designed with a focus on using modern hardware technologies to provide new features to the reverse engineering world...
[sc name=”ad_1″] Paradoxia Remote Access Tool. Features Paradoxia Console Feature Description Easy to use Paradoxia is extremely easy to use, So...
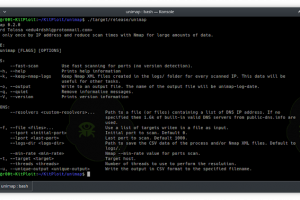
[sc name=”ad_1″] Scan only once by IP address and reduce scan times with Nmap for large amounts of data. Unimap is an abbreviation of “Unique...
[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] SkyArk is a cloud security project with two main scanning modules: AzureStealth – Scans Azure environments AWStealth –...