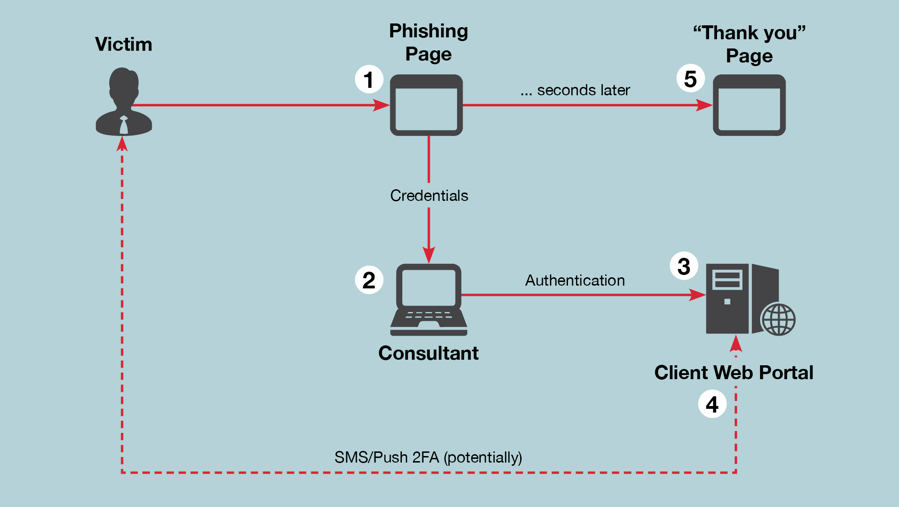
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
Search Results For - Research
Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible...
Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. It comes with pre-made...
OWASP Nettacker project is created to automate information gathering, vulnerability scanning and eventually generating a report for networks, including...
Halcyon IDE lets you quickly and easily develop scripts for performing advanced scans on applications and infrastructures with a range from recon to...
Collaborative (mitm) cryptocurrency mining pool in wifi networks. This script performs autonomous MITM attack on WiFi networks. It will inject a javascript in...
Apple has issued a statement regarding the Meltdown and Spectre vulnerabilities, confirming all Mac systems and iOS devices are affected, but saying there are...
It’s time to learn how to renew its OS because researcher James Bercegay has found a dozen models possess a hard-coded backdoor. The backdoor, lets anyone log...
Security researchers from Rhino Labs (a US-based cyber-security firm) have found that cyber criminals can use a Microsoft Word feature dubbed subDoc to fool...
The prosecutions were filed in California, Oregon, and Indiana, according to The News. The three incidents focus on the setback in Intel disclosing the...