[sc name=”ad_1″] There are many scenarios where you would want to recover deleted data from your Mac. These deleted files could be your important...
Search Results For - Real Time
[sc name=”ad_1″] Enumerate a target Based off of Nmap Results Features The purpose of O.G. Auto-Recon is to automate the initial information...
[sc name=”ad_1″] Project Axiom is a set of utilities for managing a small dynamic infrastructure setup for bug bounty and pentesting. Axiom right...
[sc name=”ad_1″] Impost3r is a tool that aim to steal many kinds of linux passwords(including ssh,su,sudo) written by C. Attackers can use Impost3r...
[sc name=”ad_1″] Please note: We take Vault’s security and our users’ trust very seriously. If you believe you have found a security...
[sc name=”ad_1″] ADCollector is a lightweight tool that enumerates the Active Directory environment to identify possible attack vectors. It will...
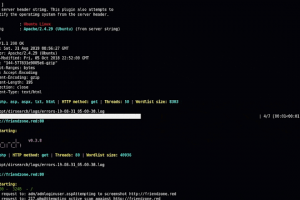
[sc name=”ad_1″] Working and learning have gone remote, and we have to come to terms with this new reality. Nowadays, several organizations allow...
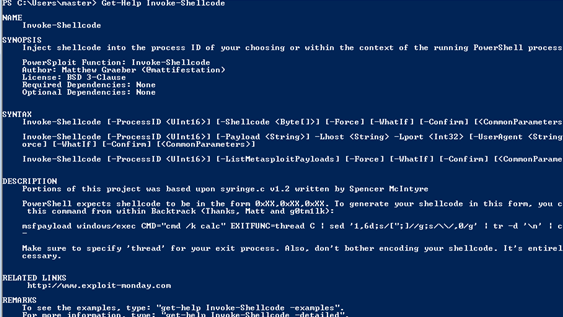
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
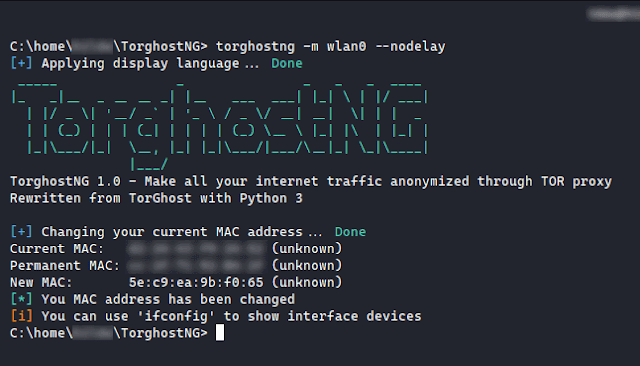
[sc name=”ad_1″] TorghostNG is a tool that make all your internet traffic anonymized through Tor network. Rewritten from TorGhost with Python 3...
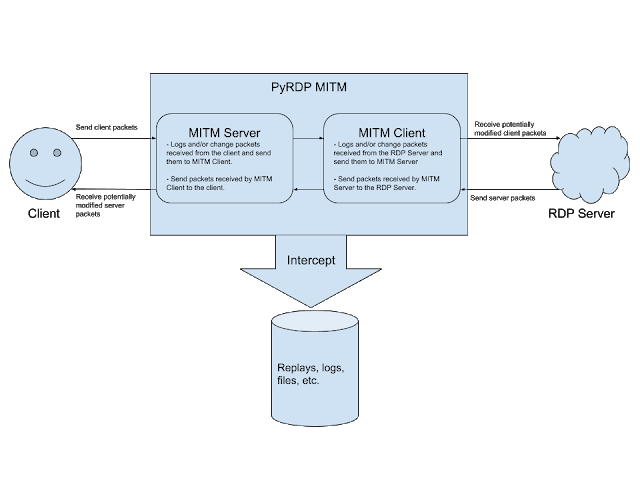
[sc name=”ad_1″] PyRDP is a Python 3 Remote Desktop Protocol (RDP) Man-in-the-Middle (MITM) and library. It features a few tools: RDP Man-in-the...