Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
Search Results For - Proof Of Concept
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
[sc name=”ad_1″] This is a proof of concept of how a ransomware works, and some techniques that we usually use to hijack our files. This project is...
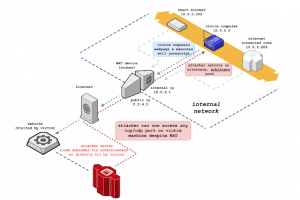
[sc name=”ad_1″] NAT Slipstreaming allows an attacker to remotely access any TCP/UDP services bound to a victim machine, bypassing the...
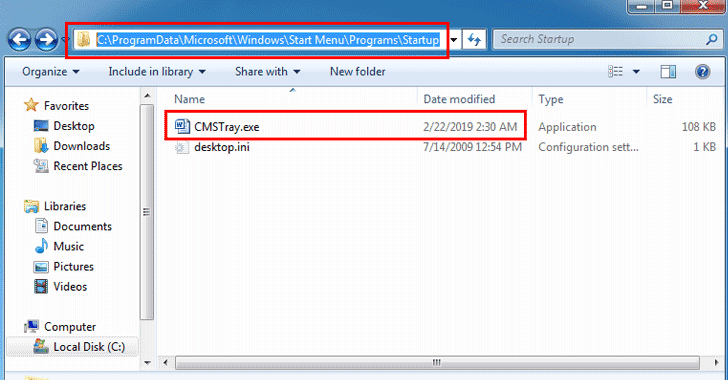
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
[sc name=”ad_1″] A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written...
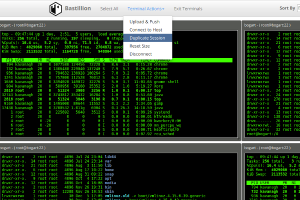
[sc name=”ad_1″] Bastillion is a web-based SSH console that centrally manages administrative access to systems. Web-based administration is...
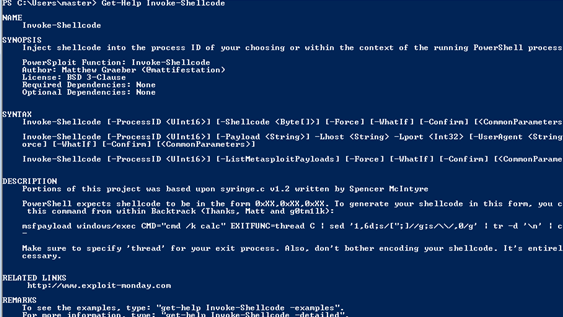
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...