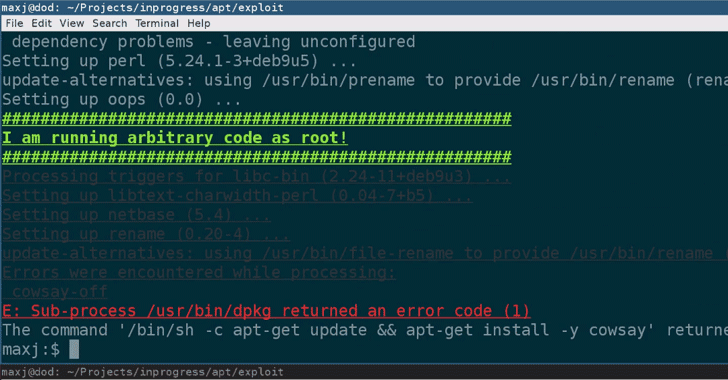
[sc name=”ad_1″] Just in time… Cybersecurity experts this week fighting over Twitter in favor of not using HTTPS and suggesting software developers...
Search Results For - Proof Of Concept
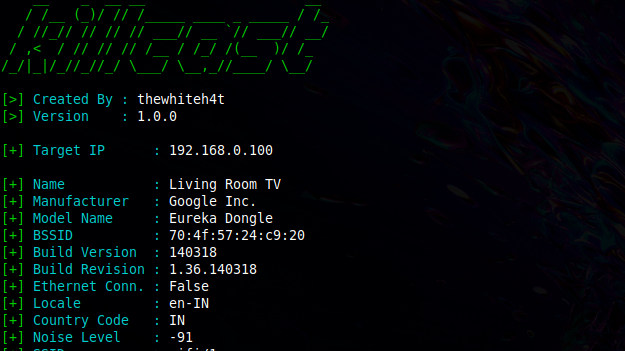
[sc name=”ad_1″] Manipulate Chromecast Devices in your Network. Inspiration – Thousands of Google Chromecast Devices Hijacked to Promote...
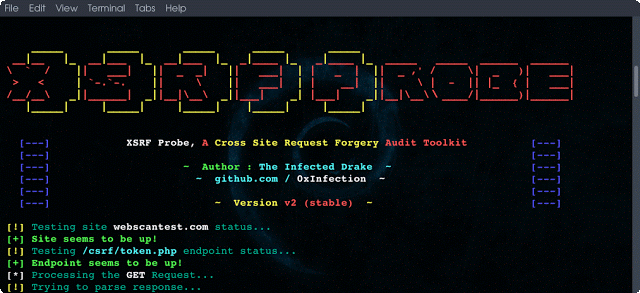
[sc name=”ad_1″] XSRFProbe is an advanced Cross Site Request Forgery (CSRF/XSRF) Audit and Exploitation Toolkit. Equipped with a Powerful Crawling...
[sc name=”ad_1″] Here we have great news for all bug bounty hunters. Now you can get paid up to $40,000 for finding and responsibly reporting...
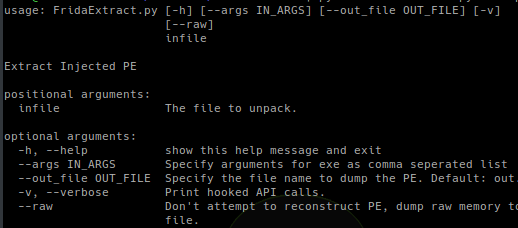
FridaExtract is a Frida.re based RunPE extraction tool. RunPE type injection is a common technique used by malware to hide code within another process. It also...
Console Application designed to interact with SharpSploit released by @cobbr_io SharpSploit is a tool written by @cobbr_io that combines many techniques/C#...
Seeker utilizes HTML5, Javascript, JQuery and PHP to grab Device Information and GeoLocation with High Accuracy. Seeker Hosts a fake website on Apache Server...
Defeating Google’s audio reCaptcha system with 85% accuracy. Inspiration Across the Internet, hundreds of thousands of sites rely on Google’s...
A security researcher (@s1guza) has published the details of an unpatched vulnerability in macOS that can be exploited to gain full control of a system. The...
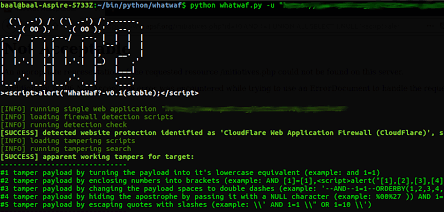
WhatWaf is an advanced firewall detection tool who’s goal is to give you the idea of “There’s a WAF?”. WhatWaf works by detecting a...