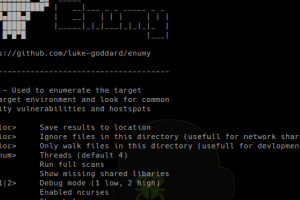
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running...
Search Results For - Post Exploitation
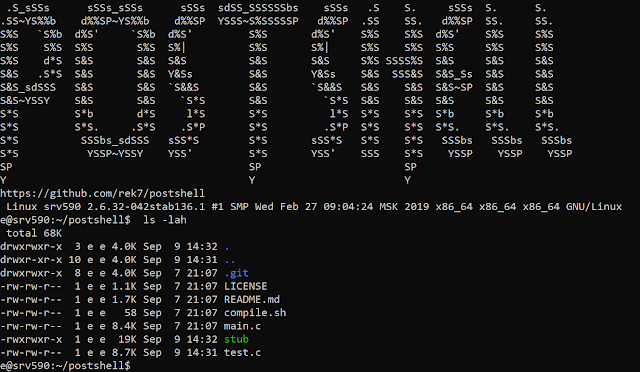
[sc name=”ad_1″] PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It creates a fully interactive TTY...
Bashark aids pentesters and security researchers during the post-exploitation phase of security audits. Usage To launch Bashark on compromised host, simply...
p0wnedShell is an offensive PowerShell host application written in C# that does not rely on powershell.exe but runs powershell commands and functions within a...
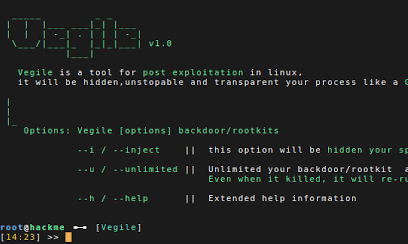
Vegile is a tool for Post exploitation Techniques in linux. Post Exploitation techniques will ensure that we maintain some level of access and can...
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
[sc name=”ad_1″] About Ghost Framework Ghost Framework is an Android post-exploitation framework that exploits the Android Debug Bridge to remotely...
[sc name=”ad_1″] DeimosC2 is a post-exploitation Command & Control (C2) tool that leverages multiple communication methods in order to control...
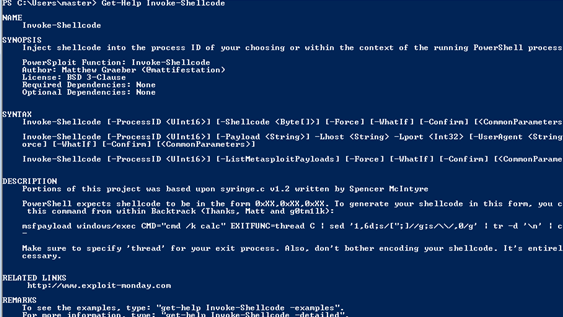
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4...