Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...
Search Results For - Phone
Device drivers are an essential part in modern Unix-like systems to handle operations on physical devices, from hard disks and printers to digital cameras and...
The Google Play store has made headlines recently when cyber criminals were able to hack in and post a fake WhatsApp messenger update for download. More than a...
Comcast verified the statements in a tweet on its customer care account. The outage seems to have begun around 1 PM ET. Some users reached intermittent or slow...
Easily launch a new phishing site fully presented with SSL and capture credentials along with 2FA tokens using CredSniper. The API provides secure access to...
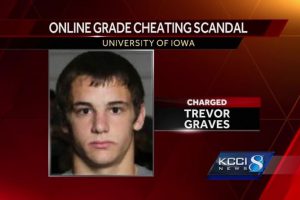
The FBI apprehended the suspect Trevor Graves, age 22 at the close of October, in Denver, his hometown. According to an FBI arrest warrant, the teen planted...
Cybercriminals are known to take advantage of everything that’s popular among people in order to spread malware, and Google’s official Play Store...
Across the Internet, hundreds of thousands of sites rely on Google’s reCaptcha system for defense against bots (in fact, Devpost uses reCaptcha when creating a...
Tweep is an advanced Twitter scraping tool written in python that allows for scraping Tweets and pictures from Twitter profiles without using Twitter’s...
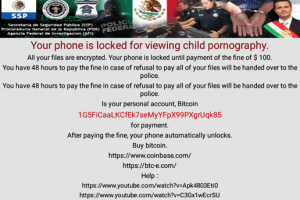
Security researchers from SfyLabs have detected an Android banking trojan dubbed LokiBot that transforms itself into a complete ransomware once the targeted...