AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
Search Results For - Opera
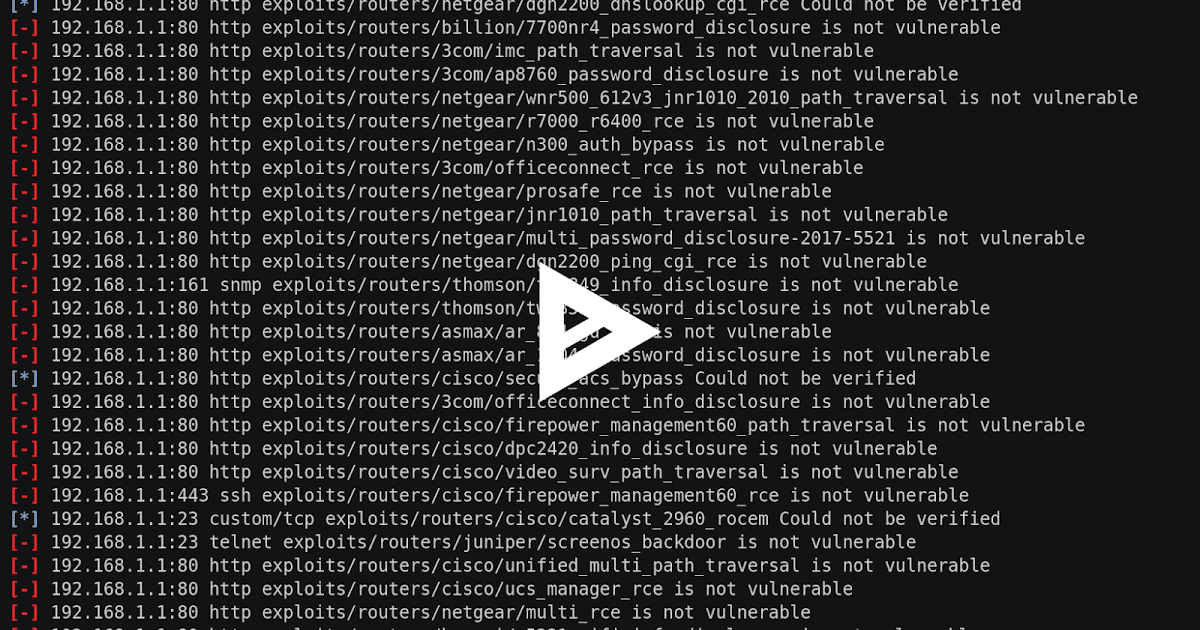
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4...
A framework based on the Fiddler web debugger to study Exploit Kits, malvertising and malicious traffic in general. Installation Download and install the...
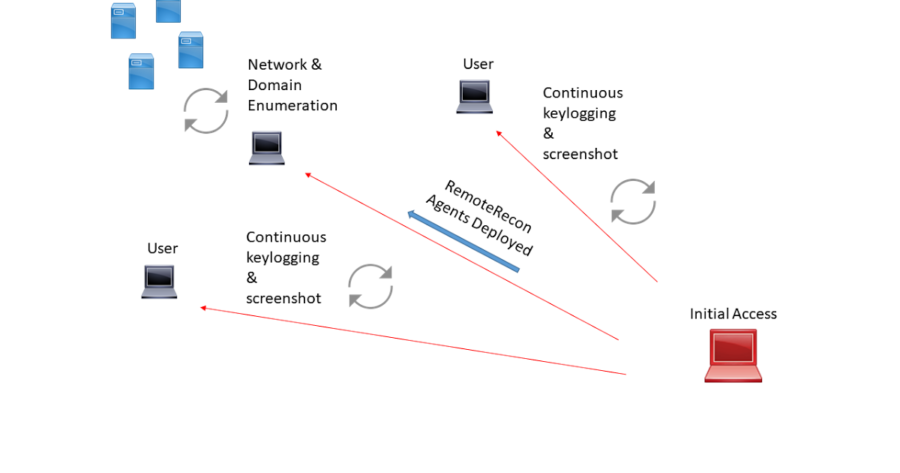
RemoteRecon provides the ability to execute post-exploitation capabilities against a remote host, without having to expose your complete toolkit/agent. Often...
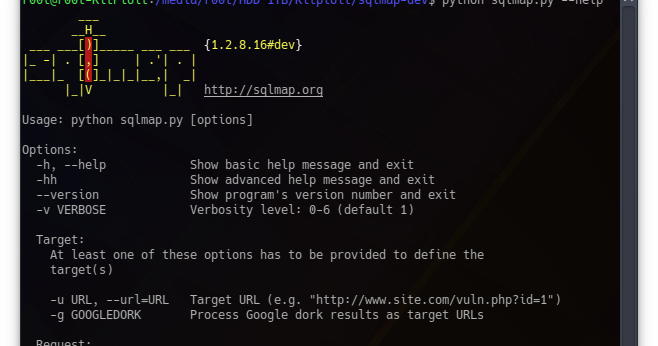
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...
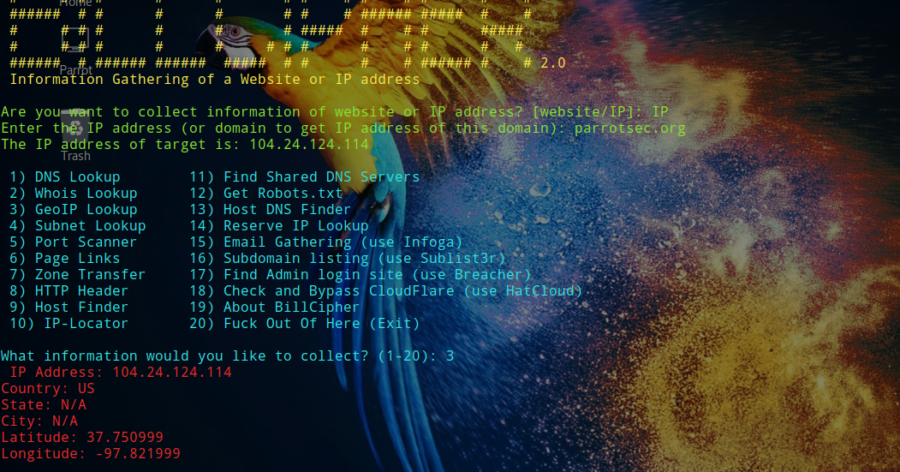
Information Gathering tool for a Website or IP address, use some ideas from Devploit. BillCipher can work in any operating system if they have and support...
What is Cindicator? Cindicator fuses together machine learning and market analysis for asset management and financial analytics. The Cindicator team dubs this...
Seeker utilizes HTML5, Javascript, JQuery and PHP to grab Device Information and GeoLocation with High Accuracy. Seeker Hosts a fake website on Apache Server...