[sc name=”ad_1″] Takeover AWS ips and have a working POC for Subdomain Takeover. Idea is simple Get subdomains. Do reverse lookups to only save AWS...
Search Results For - Linux
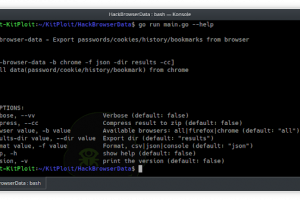
[sc name=”ad_1″] hack-browser-data is an open-source tool that could help you decrypt data (passwords / bookmarks / cookies / history) from the...
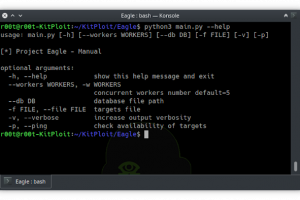
[sc name=”ad_1″] Project Eagle is a plugin based vulnerabilities scanner with threading support used for detection of low-hanging bugs on mass...
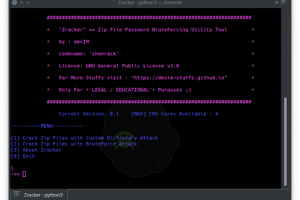
[sc name=”ad_1″] Zracker is a Zip File Password BruteForcing Utility Tool based on CPU-Power. Yet available for Linux only … Supports...
[sc name=”ad_1″] “MEDUZA” (“медуза”) means “jellyfish” in Ukrainian What is MEDUZA? It’s a Frida...
[sc name=”ad_1″] Why? If you try to learn a little bit more about crypto, either because you want to know how the attacks work or just because you...
[sc name=”ad_1″] Enumerate valid usernames from Office 365 using ActiveSync, Autodiscover, or office.com login page. Usage o365enum will read...
[sc name=”ad_1″] Nasha is a Virtual Machine for .NET files and its runtime was made in C++/CLI Installation git clone --recurse cd NashaVMNashaVM...
[sc name=”ad_1″] As indicated by sources like vulndb & cve, on a daily basis, approximately 50 new vulnerabilities become known to industry and...
[sc name=”ad_1″] IoTMap is a tool that models IoT networks using one or multiple protocols simultaneously. This is work in progress, as a part of a...