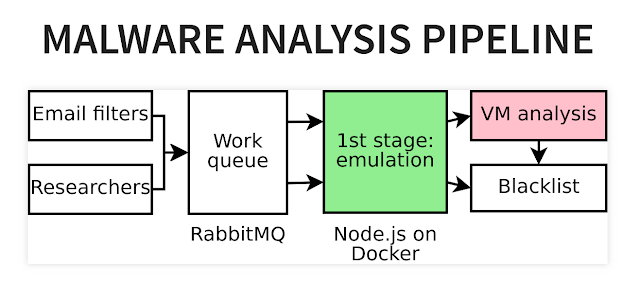
[sc name=”ad_1″] …a simple, self-contained modular host-based IOC scanner Spyre is a simple host-based IOC scanner built around the YARA...
Search Results For - Indicators of Compromise
[sc name=”ad_1″] Yeti is a platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified...
[sc name=”ad_1″] Cloud Security Operations What is Cloud Sniper? Cloud Sniper is a platform designed to manage Security Operations in cloud...
[sc name=”ad_1″] A utility to analyze malicious JavaScript. Installation Simply install box-js from npm: npm install box-js --global Usage Looking...
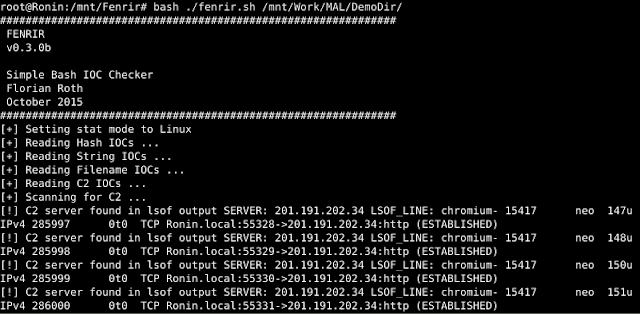
[sc name=”ad_1″] Fenrir is a simple IOC scanner bash script. It allows scanning Linux/Unix/OSX systems for the following Indicators of Compromise...
[sc name=”ad_1″] Security researchers have discovered two separate malware campaigns, one of which is distributing the Ursnif data-stealing trojan...
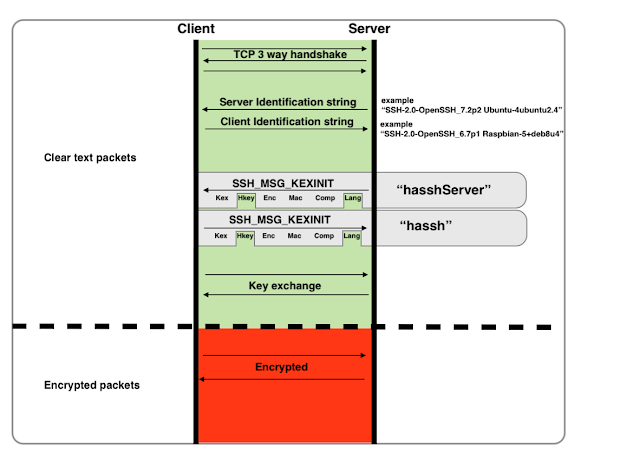
“HASSH” is a network fingerprinting standard which can be used to identify specific Client and Server SSH implementations. The fingerprints can be...
Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in...
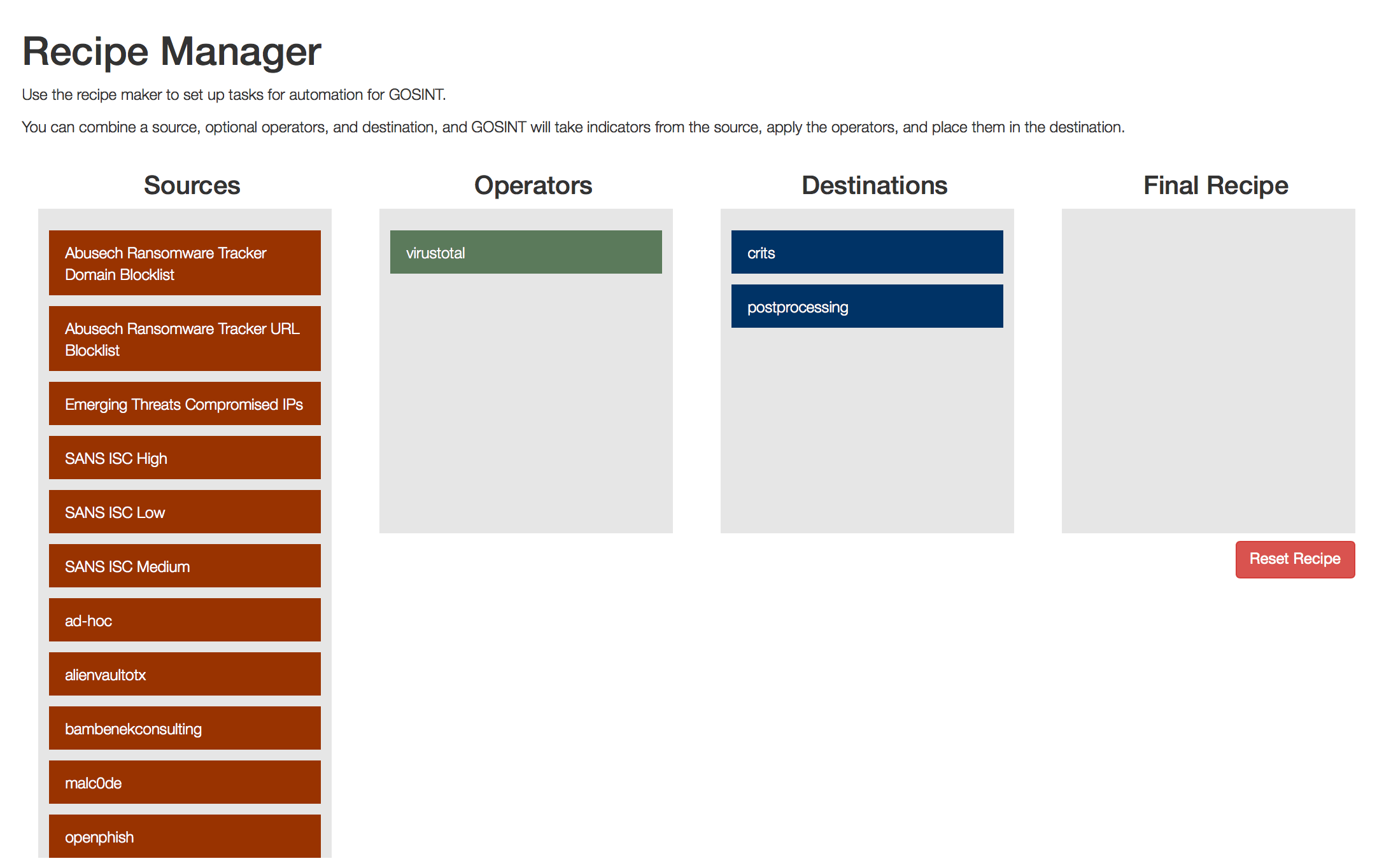
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...