[sc name=”ad_1″] Yet another PoC for Blogpost: To be used with a cmd that does whatever the F you want, for a dll that pops cmd, . check the list...
Search Results For - Hijacking
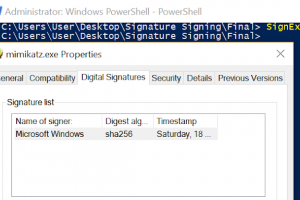
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Malicious DLL (Win Reverse Shell) generator for DLL Hijacking Features:...
[sc name=”ad_1″] URLCrazy is an OSINT tool to generate and test domain typos or variations to detect or perform typo squatting, URL hijacking...
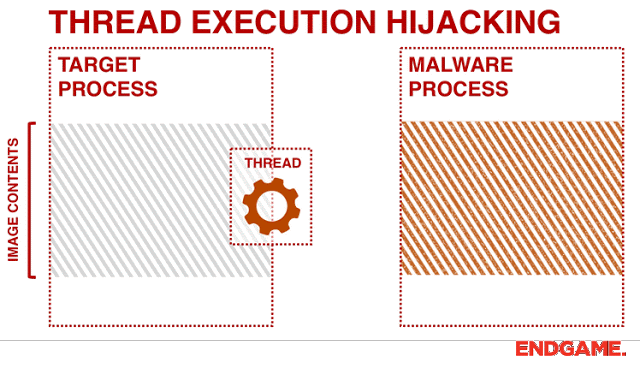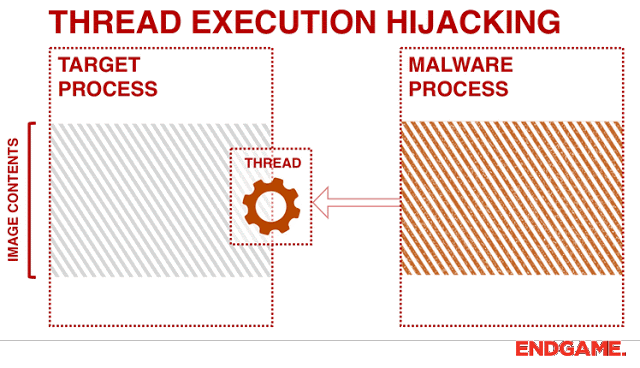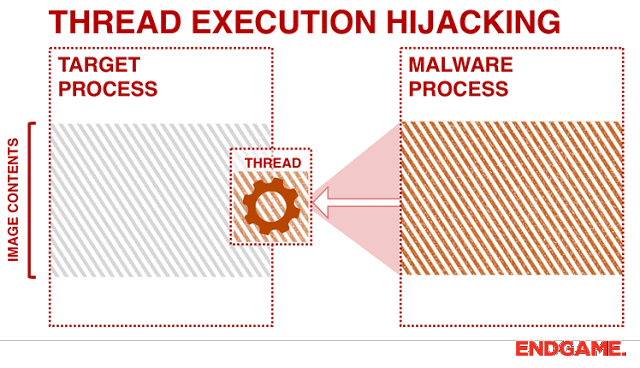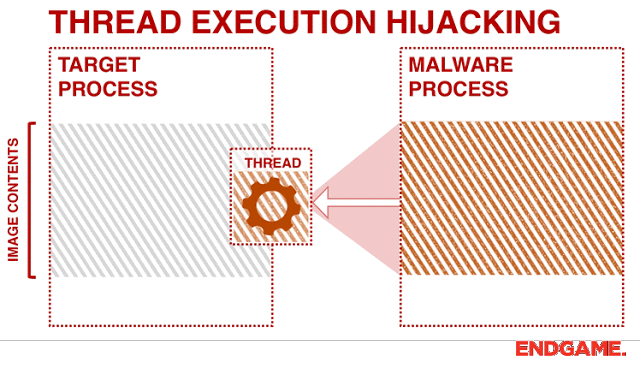
[sc name=”ad_1″] Program uses Thread Hijacking to Inject Native Shellcode into a Standard Win32 Application. With Thread Hijacking, it allows the...
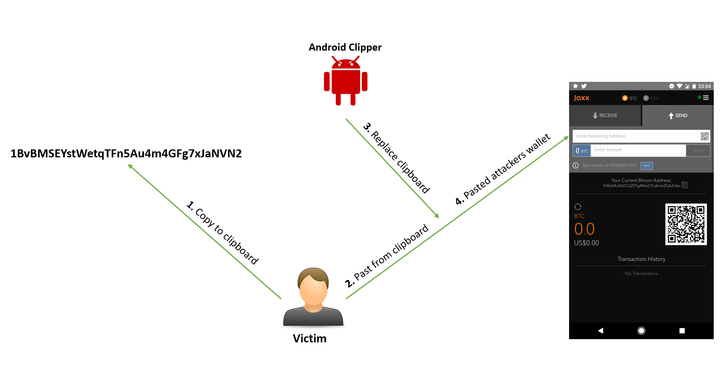
[sc name=”ad_1″] A security researcher has discovered yet another cryptocurrency-stealing malware on the official Google Play Store that was...
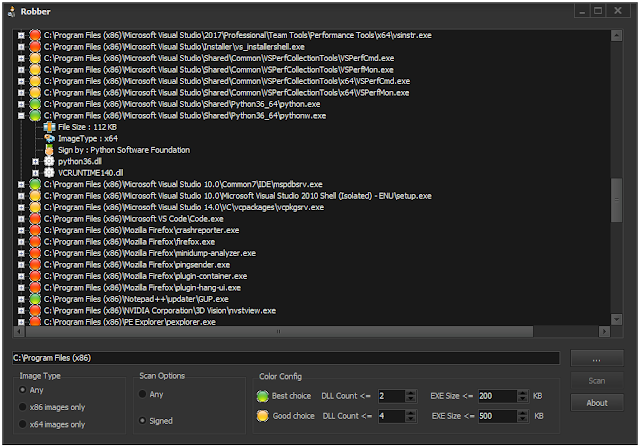
Robber is a free open source tool developed using Delphi XE2 without any 3rd party dependencies. What is DLL hijacking ?! Windows has a search path for DLLs in...
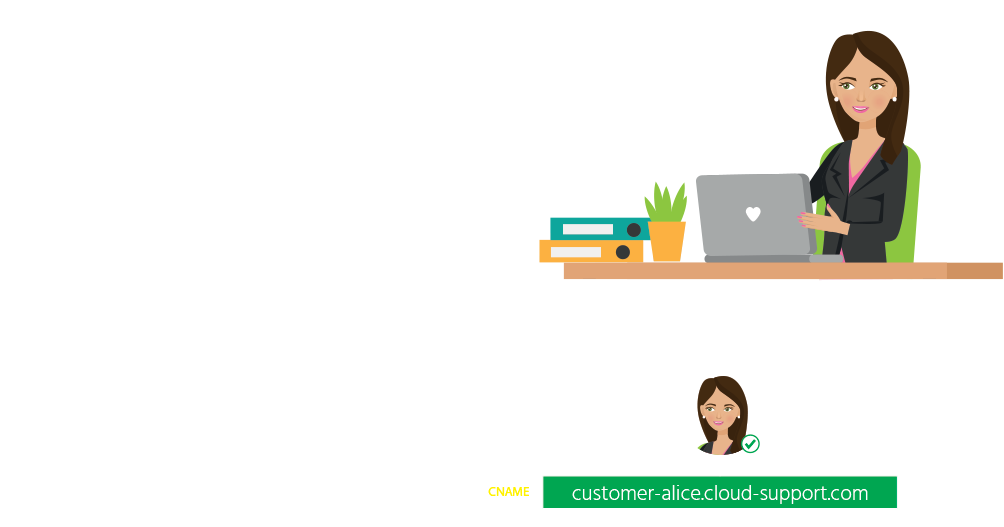
Domain Hijacking is a well-known security issue that can be carried in many different ways. In addition to social engineering or unauthorized access to the...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...