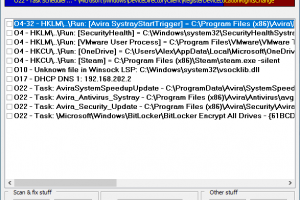
[sc name=”ad_1″] HiJackThis Fork is a free utility for Microsoft Windows that scans your computer for settings changed by adware, spyware, malware...
Search Results For - Hijacking
[sc name=”ad_1″] Widevine is a Google-owned DRM system that’s in use by many popular streaming services (Netflix, Spotify, etc.) to prevent...
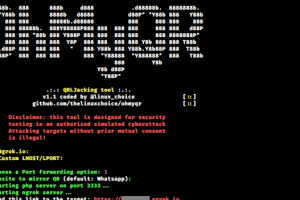
[sc name=”ad_1″] QRLJacking or Quick Response Code Login Jacking is a simple social engineering attack vector capable of session hijacking...
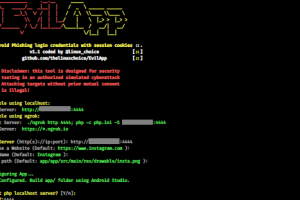
[sc name=”ad_1″] Man-in-the-middle phishing attack using an Android app to grab session cookies for any website, which in turn allows to bypass 2...
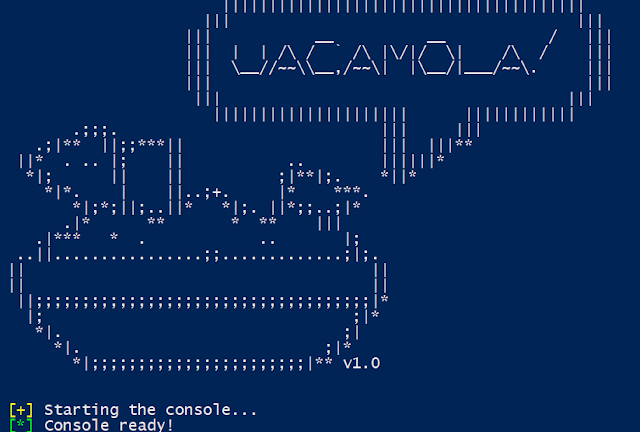
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
[sc name=”ad_1″] BOtB is a container analysis and exploitation tool designed to be used by pentesters and engineers while also being CI/CD friendly...
[sc name=”ad_1″] The popular SSH client program PuTTY has released the latest version of its software that includes security patches for 8 high...
[sc name=”ad_1″] A 20-year-old college student who stole cryptocurrency worth more than $5 million by hijacking victims’ phone numbers has...
[sc name=”ad_1″] The U.S. Department of Homeland Security (DHS) has today issued an “emergency directive” to all federal agencies...
[sc name=”ad_1″] Google, the FBI, ad-fraud fighting company WhiteOps and a collection of cyber security companies worked together to shut down one...