[sc name=”ad_1″]
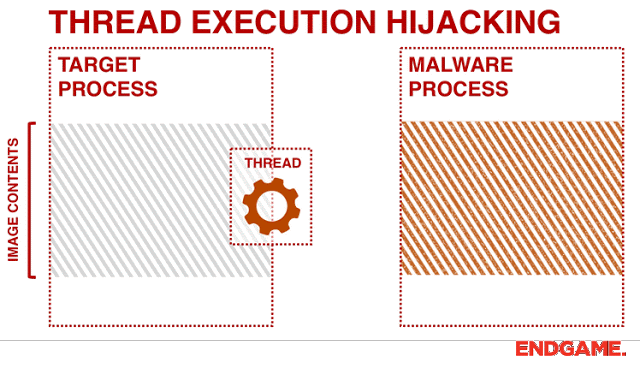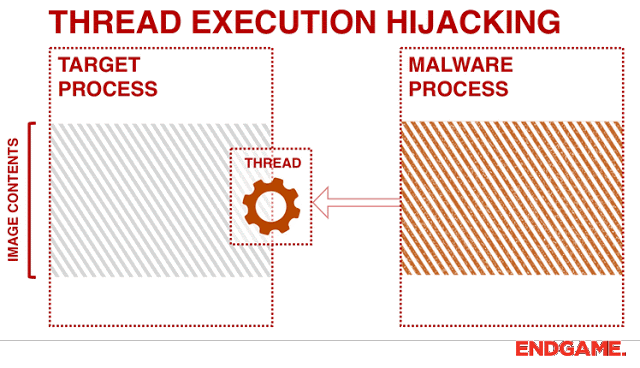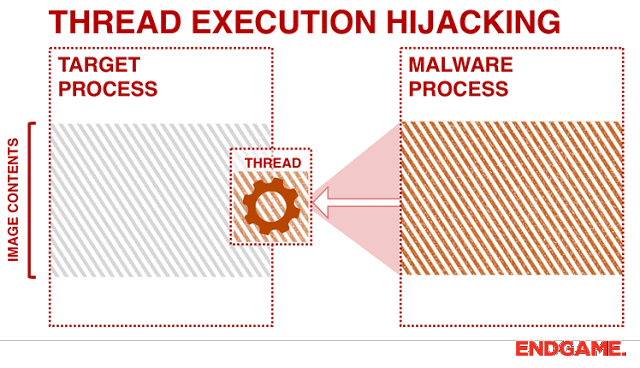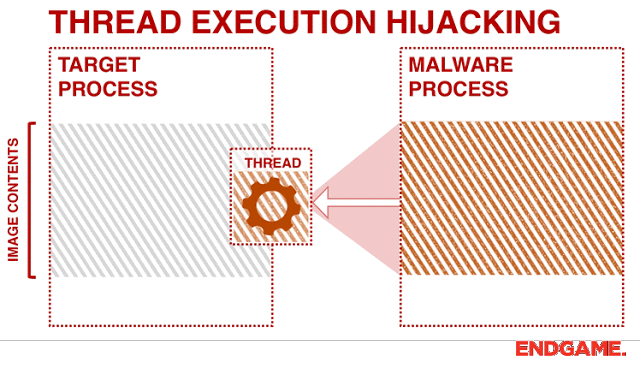
Program uses Thread Hijacking to Inject Native Shellcode into a Standard Win32 Application.
With Thread Hijacking, it allows the hijacker.exe program to suspend a thread within the target.exe program allowing us to write shellcode to a thread.
Usage
int main()
{
System sys;
Interceptor incp;
Exception exp;
sys.returnVersionState();
if (sys.returnPrivilegeEscalationState())
{
std::cout << "Token Privileges Adjusted\n";
}
if (DWORD m_procId = incp.FindWin32ProcessId((PCHAR)m_win32ProcessName))
{
incp.ExecuteWin32Shellcode(m_procId);
}
system("PAUSE");
return 0;
}
Environment
- Windows Vista+
- Visual C++
Libs
- Winapi
- user32.dll
- kernel32.dll
- ntdll.dll
[sc name=”ad-in-article”]




















Add Comment