Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
Search Results For - Hidden
CHAOS allow generate payloads and control remote Windows systems. Features Reverse Shell Download File Upload File Screenshot ? Keylogger ? Persistence Open...
Deplug is a graphical network analyzer powered by web technologies. Features Cross-Platform (macOS, Linux, Windows) Web-based UI (Electron) Built-in Package...
XSStrike is an advanced XSS detection and exploitation suite. It has a powerful fuzzing engine and provides zero false positive result using fuzzy matching...
Embomber is a Python Script for Email Bombing which supports Gmail, Yahoo, Hotmail/Outlook In Internet usage, an email bomb is a form of net abuse consisting...
Author: Alex Moskov What is Litecoin? Litecoin (LTC) is a decentralized peer-to-peer cryptocurrency that was released on October 7th, 2011 and went live on...
Python script that gets Twitter users’ tweets location Features Gets Twitter Usernames based on a latitude and longitude Profiles URLs Tweet Latitude and...
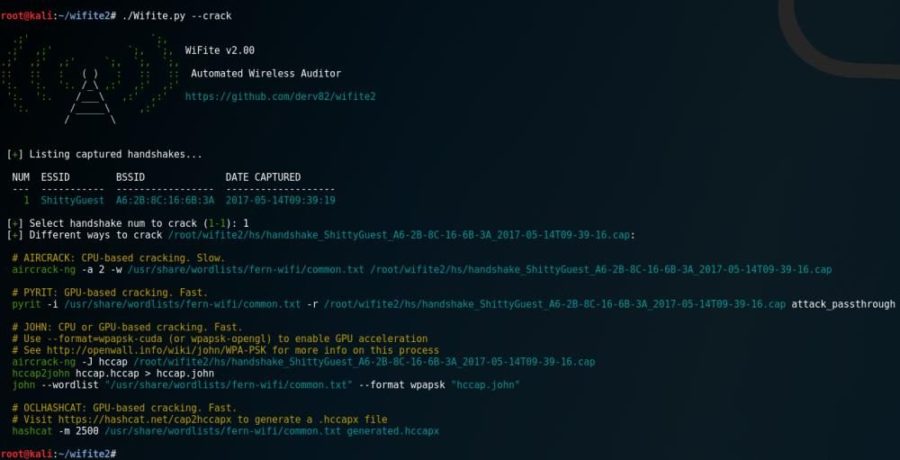
Wifite is a Python script for auditing wireless networks which aims to be the “set it and forget it” wireless auditing tool. What’s new in Wifite 2...
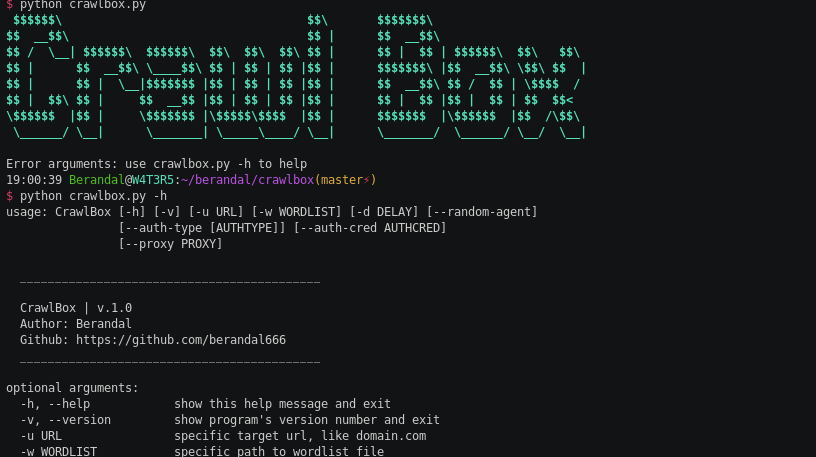
Easy way to brute-force web directory. Operating Systems Tested: MacOSX Kali Linux Usage: python crawlbox.py [-h] [-v] [-w WORDLIST] url positional arguments:...
[sc name=”ad_1″] Hacking a Wi-Fi network using Kali Linux needs a wireless card that support monitor mode and packet injection. Not all wireless...