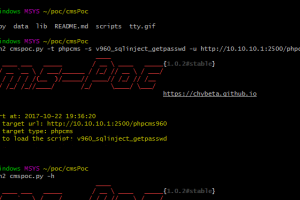
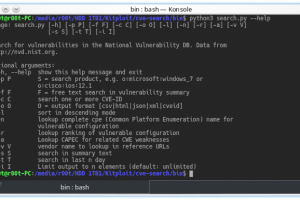
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Search Results For - Exploitation
Dr. Matthew Falder, 28, of Birmingham, England is at the center of one of the most horrific crimes law enforcement has come across on the Darknet. Falder has...
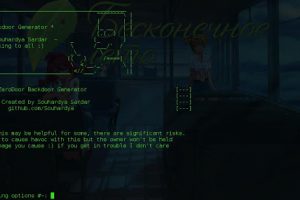
Hey Guys, In this video i show you a cool script called ZeroDoor which used for Generating Cross-Platform Backdoors. ZeroDoor: A script written lazily for...
Legal Disclaimer: This project is made for educational and ethical testing purposes only。It is the end user’s responsibility to obey all applicable local...
A script written lazily for generating reverse shell backdoors on the go whenever you need without any hassle for your daily penetration needs . These...
Bash script purposed for system enumeration, vulnerability identification and privilege escalation. MIDA Multitool draws functionality from several of my...
A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack...
Security researchers have discovered several key management vulnerabilities in the core of Wi-Fi Protected Access II (WPA2) protocol that could allow an...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...