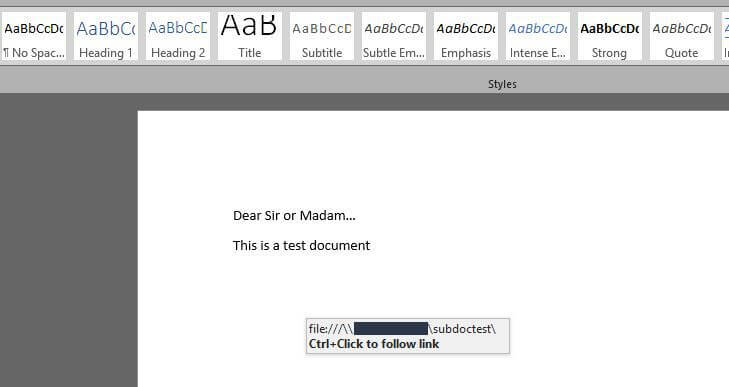
Security researchers from Rhino Labs (a US-based cyber-security firm) have found that cyber criminals can use a Microsoft Word feature dubbed subDoc to fool...
Search Results For - Exploitation
A Penetration Testing Framework, you will have every script that a hacker needs Fsociety: Menu Information Gathering Password Attacks Wireless Testing...
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
The PowerUpSQL module includes functions that support SQL Server discovery, auditing for common weak configurations, and privilege escalation on scale. It is...
ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that...
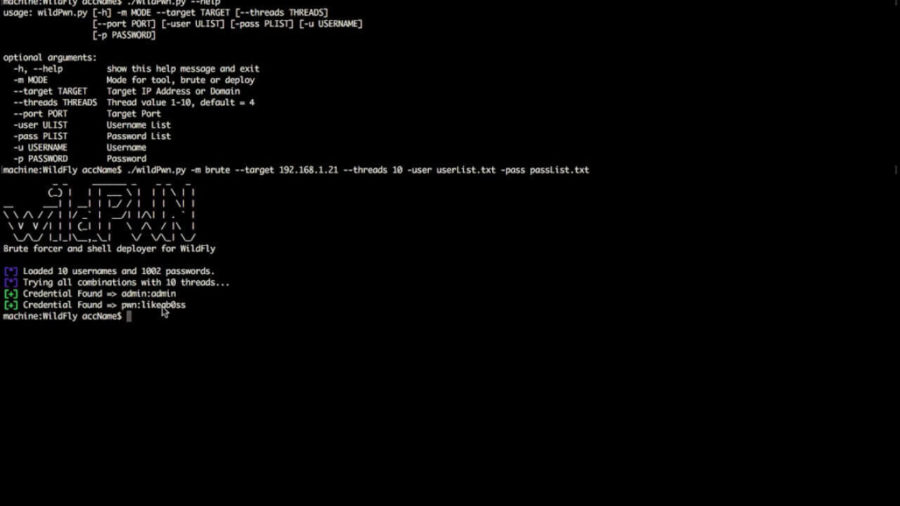
WildFly, formerly known as JBoss AS, or simply JBoss, is an application server authored by JBoss, now developed by Red Hat. WildFly is written in Java, and...
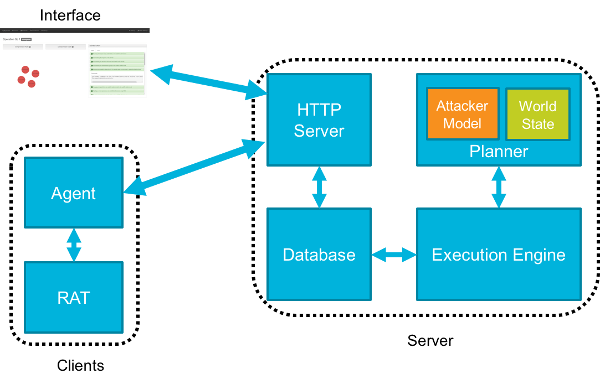
CALDERA is an automated adversary emulation system that performs post-compromise adversarial behavior within enterprise networks. It generates plans during...
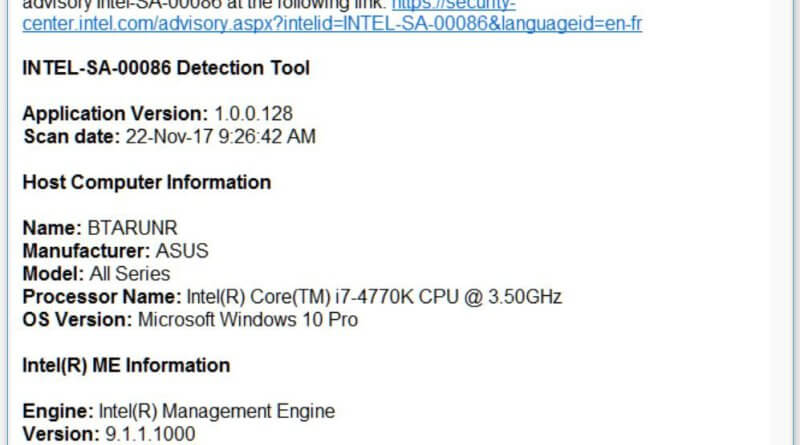
These ME security holes affect millions of computers. ME continues Intel’s Active Management Technology (AMT). This is a great tool that allows admins to...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
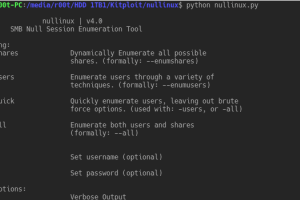
nullinux is an internal penetration testing tool for Linux that can be used to enumerate OS information, domain information, shares, directories, and users...