[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
Search Results For - Endpoints
[sc name=”ad_1″] Bug Bounty Recon (bbrecon) is a free Recon-as-a-Service for bug bounty hunters and security researchers. The API aims to provide a...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
[sc name=”ad_1″] A multi-threaded AWS inventory collection tool. The creators of this tool have a recurring need to be able to efficiently collect...
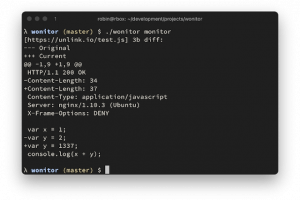
[sc name=”ad_1″] fast, zero config web endpoint change monitor. for comparing responses, a selected list of http headers and the full response body...
[sc name=”ad_1″] Sinter is a 100% user-mode endpoint security agent for macOS 10.15 and above, written in Swift. Sinter uses the user-mode...
[sc name=”ad_1″] CWFF is a tool that creates a special High quality fuzzing/content discovery wordlist for you at the highest speed possible using...
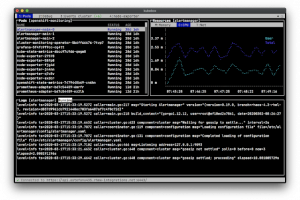
[sc name=”ad_1″] Terminal and Web console for Kubernetes Features Configuration from kubeconfig files (KUBECONFIG environment variable or $HOME/...
[sc name=”ad_1″] Security Tool for Reconnaissance and Information Gathering on a website. (python 2.x & 3.x) This script use...