[sc name=”ad_1″] Blog can be found at Script made for all your javascript recon automation in bugbounty. Just pass subdomain list to it and options...
Search Results For - Endpoints
[sc name=”ad_1″] We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to public, where products and...
[sc name=”ad_1″] Based on pywebfuzz, Py3webfuzz is a Python3 module to assist in the identification of vulnerabilities in web applications, Web...
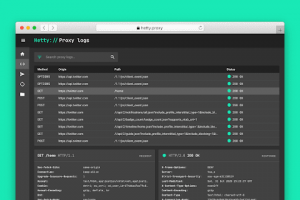
[sc name=”ad_1″] Hetty is an HTTP toolkit for security research. It aims to become an open source alternative to commercial software like Burp...
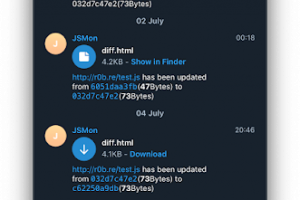
[sc name=”ad_1″] Using this script, you can configure a number of JavaScript files on websites that you want to monitor. Everytime you run this...
[sc name=”ad_1″] Instagram offers two kinds of APIs to developers. The Instagram API Platform (extremely limited in functionality and close to...
[sc name=”ad_1″] GWTMap is a tool to help map the attack surface of Google Web Toolkit (GWT) based applications. The purpose of this tool is to...
[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
[sc name=”ad_1″] What’s AutoGadgetFS ? AutoGadgetFS is an open source framework that allows users to assess USB devices and their associated...
[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...