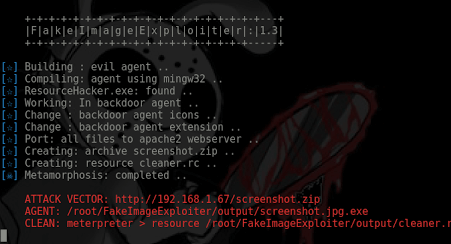
This module takes one existing image.jpg and one payload.ps1 (input by user) and builds a new payload (agent.jpg.exe) that if executed it will trigger the...
Search Results For - DDE
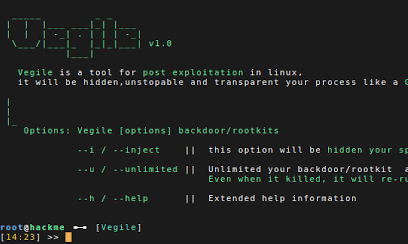
Vegile is a tool for Post exploitation Techniques in linux. Post Exploitation techniques will ensure that we maintain some level of access and can...
Spectre & Meltdown Checker A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs...
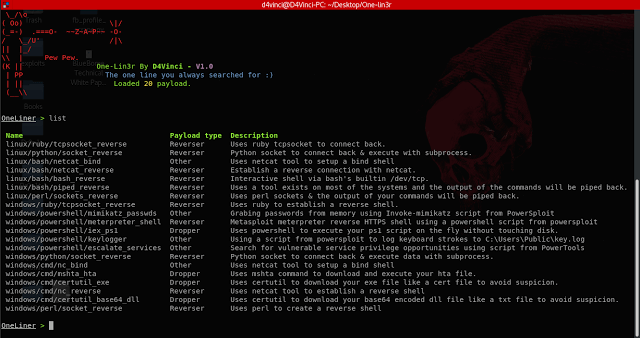
One-Lin3r is simple and light-weight framework inspired by the web-delivery module in Metasploit. It consists of various one-liners that aids in penetration...
The CEO of one of the world’s prominent chipmakers, Brian Krzanich of Intel, took to the platform at a keynote at CES to say a few messages about the news...
The malicious software uncovered pornographic ads and attempted to trick users into buying added services, according to Check Point. “We’ve eliminated the apps...
CS Suite is a one stop tool for auditing the security posture of the AWS infrastructure and does system audits as well. CS Suite leverages current open source...
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
NXcrypt is a polymorphic ‘python backdoors’ crypter written in python by Hadi Mene (h4d3s) . The output is fully undetectable. NXcrypt can inject...
Salamandra is a tool to detect and locate spy microphones in closed environments. It find microphones based on the strength of the signal sent by the...