Salamandra is a tool to detect and locate spy microphones in closed environments. It find microphones based on the strength of the signal sent by the microphone and the amount of noise and overlapped frequencies. Based on the generated noise it can estimate how close or far away you are from the microphone.
Installation
USB SDR Device
To use Salamandra you nee to have a SDR (Software Define Radio) device. It can be any from the cheap USB devices, such as this.
rtl_power software
Salamandra needs the rtl_power software installed in your computer. To install it you can do:
- On MacOS:sudo port install rtl-sdr
If you don’t have ports in your MAC, see port installation
- On Linux:apt-get install rtl-sdr
- On Windows: See http://www.rtl-sdr.com/getting-the-rtl-sdr-to-work-on-windows-10/
If rtl_power was installed correctly, you should be able to run this command in any console:
rtl_test
And you should see one device detected.
Usage
Basic usage for detecting microphones
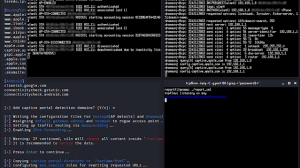
./salamandra.py
This command will use a default threshold of 10.8, a min freq of 100Mhz, a max freq of 400Mhz and sound. You can change the default values with parameters.
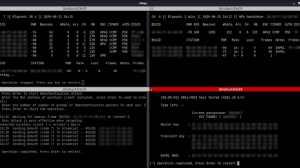
Location Mode to find Hidden Microphones
- Run Salamandra with a threshold of 0, starting in the frequency 100MHz and ending in the frequency 200MHz. Search is activated with (-s). And make sounds (-S)./salamandra.py -t 0 -a 100 -b 200 -s -S
Location Mode from a stored rtl_power file
./salamandra.py -t 0 -a 111 -b 113 -s -f stored.csv
To actually create the file with rtl_power, from 111MHz to 114MHz, with 4000Khz step, gain of 25, integration of 1s and capturing for 5min, you can do:
rtl_power -f 111M:114M:4000Khz -g 25 -i 1 -e 300 stored.csv



















Add Comment