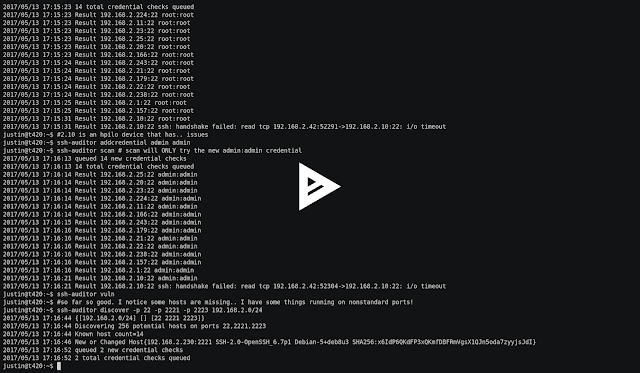
The Best Way To Scan For Weak Ssh Passwords On Your Network Features ssh-auditor will automatically: Re-check all known hosts as new credentials are added. It...
Search Results For - Compiler
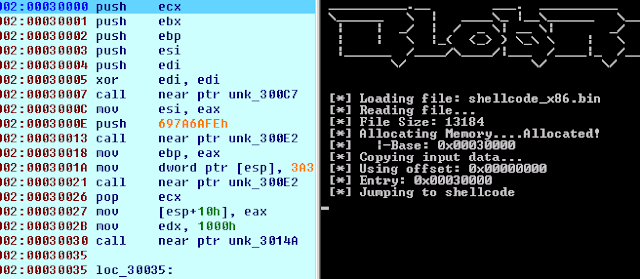
BlobRunner is a simple tool to quickly debug shellcode extracted during malware analysis. BlobRunner allocates memory for the target file and jumps to the base...
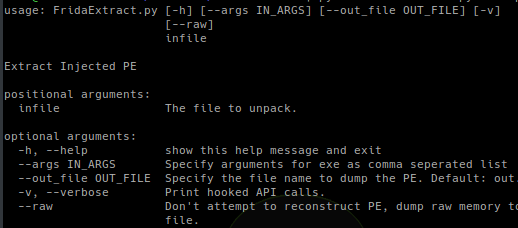
FridaExtract is a Frida.re based RunPE extraction tool. RunPE type injection is a common technique used by malware to hide code within another process. It also...
Google has added a new security feature to the latest Linux kernels for Android devices to prevent it against code reuse attacks that allow attackers to...
Slither is a Solidity static analysis framework written in Python 3. It runs a suite of vulnerability detectors, prints visual information about contract...
A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4...
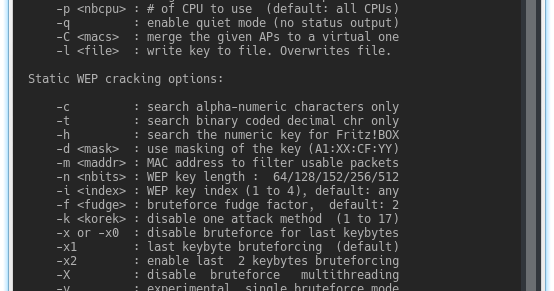
Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet capture and export...
Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
Spectre & Meltdown Checker A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs...
Microsoft is addressing unusual of the performance subdividing for fixing patches to relieve the Meltdown and Spectre vulnerabilities. Windows Chief Terry...