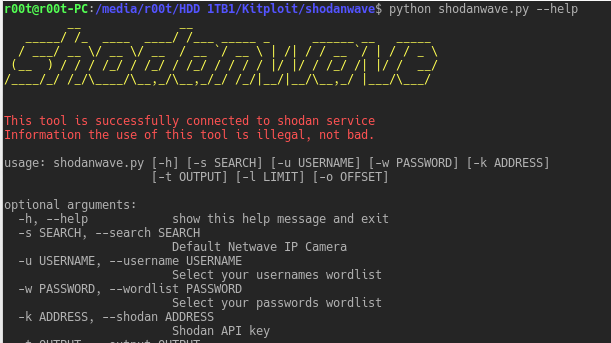
Shodanwave is a tool for exploring and obtaining information from cameras specifically Netwave IP Camera. The tool uses a search engine called shodan that...
Search Results For - Access
It’s the latest movement in a clash between Amazon and Google, which has seen the two businesses hold their products off the rival’s programs and services...
Some work has been already published regarding the subject of cryptograhic keys security within DRAM. Basically, we need to find something that looks like a...
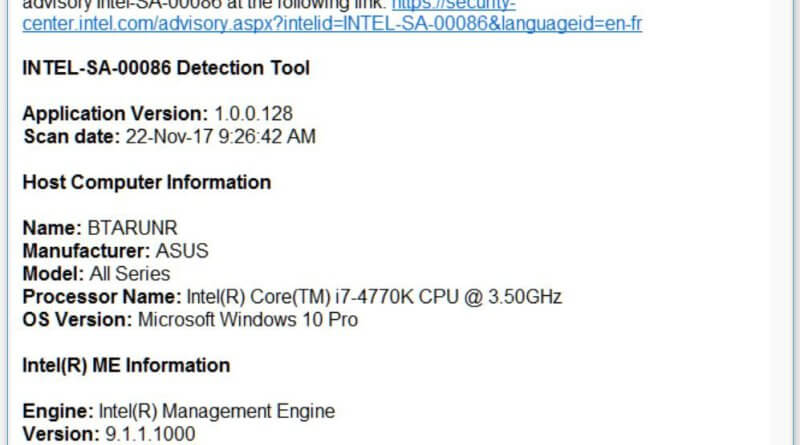
These ME security holes affect millions of computers. ME continues Intel’s Active Management Technology (AMT). This is a great tool that allows admins to...
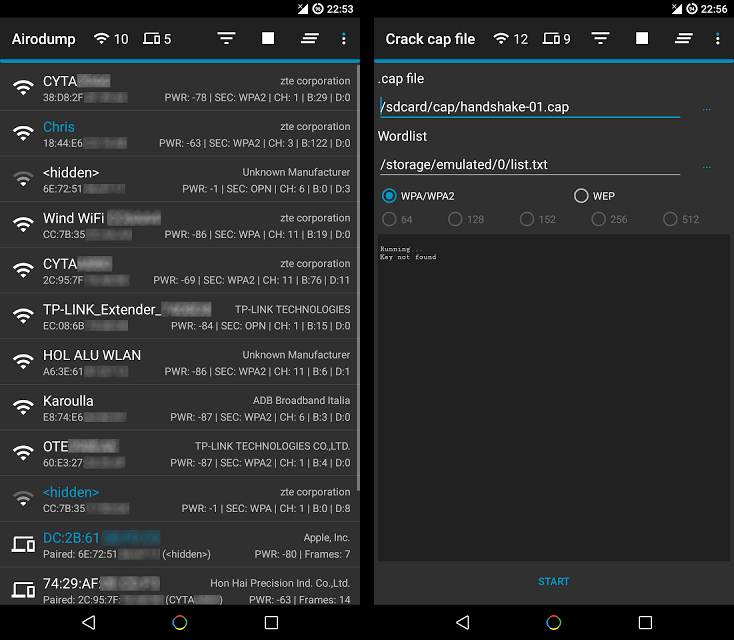
Hijacker is a Graphical User Interface for the penetration testing tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. It offers a simple and easy UI to use these...
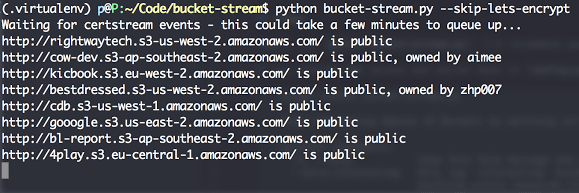
Some quick tips if you use S3 buckets: Randomise your bucket names! There is no need to use company-backup.s3.amazonaws.com. Set appropriate permissions and...
A former National Security Agency hacker has admitted to illegally taking highly classified information from the agency’s headquarters, which was later...
After rapidly reinforcing a flaw that acknowledged anyone with access to a High Sierra Mac to take administrative control, Apple still has extra work to do to...
sslh accepts connections on specified ports, and forwards them further based on tests performed on the first data packet sent by the remote client. Probes for...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...