One of the biggest names in IT industry, Intel, has verified a report stating that some microprocessors have been built containing flaws in their design...
Search Results For - Access
In today’s world, no company is fully safe as even big names like Sony and HBO have been hacked, and quite recently Nintendo’s Switch had to go through the...
Alphonso, a startup that retails media-viewing data, provides a plugin that listens for audio signals in shows and movies. Approximately 250 mobile...
Quite recently, the founder of Mcafee company, John Mcafee, was in news when his Twitter was hacked by an unknown hacker. This hacker used John’s social media...
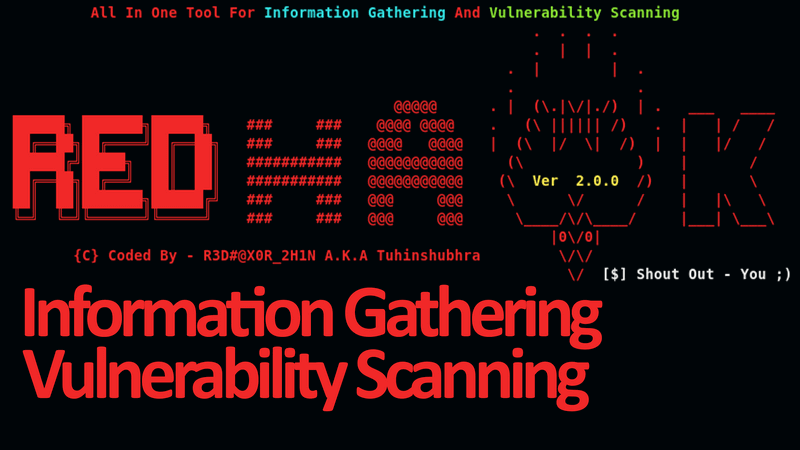
All in one tool for Information Gathering and Vulnerability Scanning RED HAWK : Scans That You Can Perform Using RED HAWK : Basic Scan Site Title NEW IP...
NTU researchers have revealed that smartphones can now be hacked using the data accumulated from sensors. Dr. Shivam, a scientist at NTU, who recently...
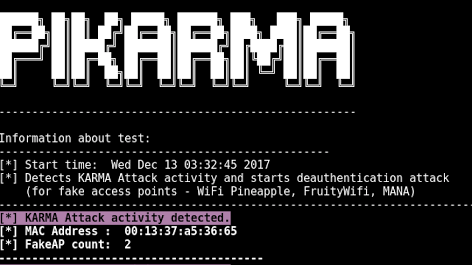
Detects wireless network attacks performed by KARMA module (fake AP). Starts deauthentication attack (for fake access points) Working Principle for PiKarma...
Russian ATMs Are Hackable It was recently revealed that some ATMs that are running in Russia are still operating on Windows XP operating system, which is why...
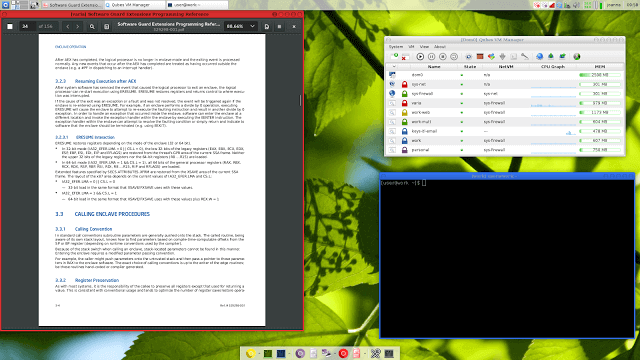
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
“This is the start of a long legal battle. Netflix stands w/ innovators, large & small, to oppose this confused FCC order,” the company tweeted quickly...