MAC Changer is an utility that makes the maniputation of MAC addresses of network interfaces easier. A media access control (Mac) address of a device is a...
Search Results For - Access
ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that tests the security of Oracle Databases remotely. Usage examples of ODAT:...
Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) connected to the internet using a variety of...
Kali Linux 2018.1 the first release of 2018, this fine release contains all updated packages and bug fixes since our 2017.3 release last November. This release...
Grouper is a slightly wobbly PowerShell module designed for pentesters and redteamers (although probably also useful for sysadmins) which sifts through the...
Sigma is a generic and open signature format that allows you to describe relevant log events in a straight forward manner. The rule format is very flexible...
Centralized firewall control provides a centralized way to manage the firewall on multiple servers or loadbalancers running iptables. This way you can quickly...
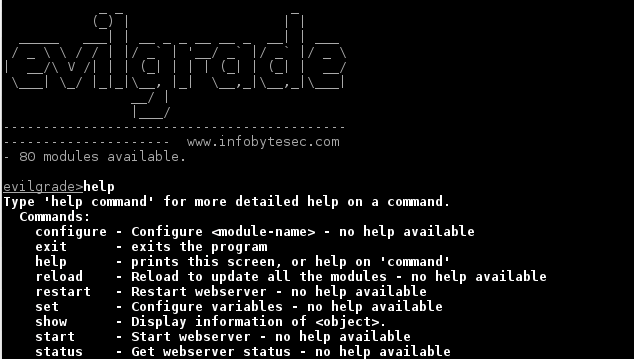
Evilgrade is a modular framework that allows the user to take advantage of poor upgrade implementations by injecting fake updates. It comes with pre-made...
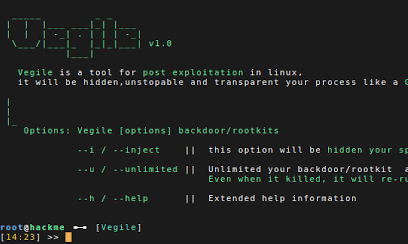
Vegile is a tool for Post exploitation Techniques in linux. Post Exploitation techniques will ensure that we maintain some level of access and can...
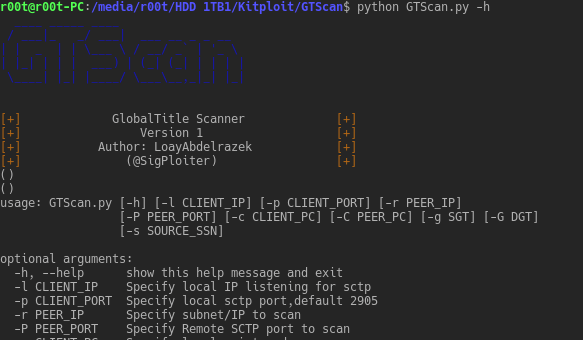
The Nmap Scanner for Telco. With the current focus on telecom security, there used tools in day to day IT side penetration testing should be extended to...