The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
Search Results For - AWS
What is Subdomain Takeover? Subdomain takeover is a class of vulnerability where subdomain points to an external service that has been deleted. The external...
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...
What is Cindicator? Cindicator fuses together machine learning and market analysis for asset management and financial analytics. The Cindicator team dubs this...
Devploit is a simple python script to Information Gathering. Download: git clone How to use: cd Devploit chmod +x install ./install Run in Terminal Devploit...
GlobaLeaks is open-source / free software intended to enable secure and anonymous whistleblowing initiatives developed by the Hermes Center for Transparency...
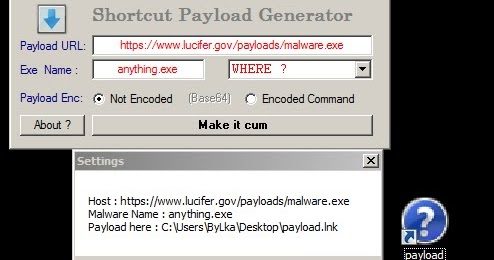
Making FUD Shortcut (.lnk) payloads with LNK-KISSER to remote execute malicious code. Shortcut-Payload-Generator Exploiting Powershell to make ShortCut...
Pwnie Island is a limited-release, first-person, true open-world MMORPG set on a beautiful island where anything could happen. That’s because this game...
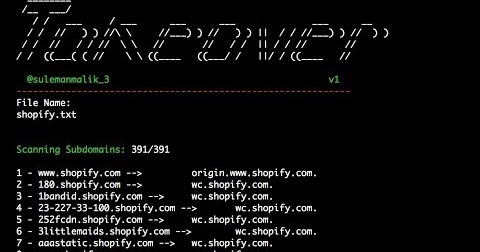
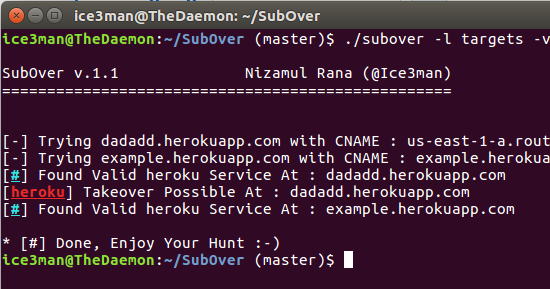
[sc name=”ad_1″] Subover is a Hostile Subdomain Takeover tool originally written in python but rewritten from scratch in Golang. Since it’s...
Interview: Aragon’s Luis Cuende on Blockchain Governance & Digital Jurisdictions Author: Bennett Garner Bennett Garner: You’ve said “humans enforce...