[sc name=”ad_1″]
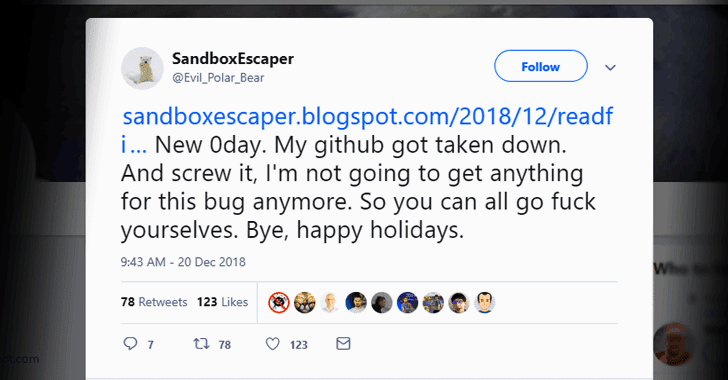
A security researcher with Twitter alias SandboxEscaper today released proof-of-concept (PoC) exploit for a new zero-day vulnerability affecting Microsoft’s Windows operating system.
SandboxEscaper is the same researcher who previously publicly dropped exploits for two Windows zero-day vulnerabilities, leaving all Windows users vulnerable to the hackers until Microsoft patched them.
The newly disclosed unpatched Windows zero-day vulnerability is an arbitrary file read issue that could allow a low-privileged user or a malicious program to read the content of any file on a targeted Windows computer that otherwise would only be possible via administrator-level privileges.
The zero-day vulnerability resides in “MsiAdvertiseProduct” function of Windows that’s responsible for generating “an advertise script or advertises a product to the computer and enables the installer to write to a script the registry and shortcut information used to assign or publish a product.”
According to the researcher, due to improper validation, the affected function can be abused to force installer service into making a copy of any file as SYSTEM privileges and read its content, resulting in arbitrary file read vulnerability.
[youtube https://www.youtube.com/watch?v=x4P2H64GI1o]
“Even without an enumeration vector, this is still bad news, because a lot of document software, like office, will actually keep files in static locations that contain the full path and file names of recently opened documents..,” the researcher said.
“Thus by reading files like this, you can get filenames of documents created by other users.. the filesystem is a spiderweb and references to user-created files can be found everywhere.. so not having an enumeration bug is not that big of a deal.”
Besides sharing video demonstration of the vulnerability, SandboxEscaper also posted a link to a Github page hosting its proof-of-concept (PoC) exploit for the third Windows zero-day vulnerability, but the researcher’s GitHub account has since been taken down.
This is the third time in the past few months SandboxEscaper has leaked a Windows zero-day vulnerability.
In October, SandboxEscaper released a PoC exploit for a privilege escalation vulnerability in Microsoft Data Sharing that allowed a low privileged user to delete critical system files from a targeted Windows system.
In late August, the researcher exposed details and PoC exploit for a local privilege escalation flaw in Microsoft Windows Task Scheduler occurred due to errors in the handling of the Advanced Local Procedure Call (ALPC) service.
Shortly after the PoC released, the then-zero-day vulnerability was found actively being exploited in the wild, before Microsoft addressed it in the September 2018 Security Patch Tuesday Updates.
http://platform.twitter.com/widgets.js
//l&&!o&&(jQuery.ajax({url:”https://thehackernews.com/feeds/posts/default?alt=json-in-script&max-results=4″,type:”get”,cache:!1,dataType:”jsonp”,success:function(e){for(var t=”http://thehackernews.com/”,r=”http://thehackernews.com/”,s=0;s<e.feed.entry.length;s++){for(var a=0;a<e.feed.entry[s].link.length;a++)if("alternate"==e.feed.entry[s].link[a].rel){t=e.feed.entry[s].link[a].href;break}if("content"in e.feed.entry[s])var n=e.feed.entry[s].content.$t;else n="summary"in e.feed.entry[s]?e.feed.entry[s].summary.$t:"http://thehackernews.com/";100<(n=n.replace(/]*>/g,”http://thehackernews.com/”)).length&&(n=n.substring(0,90));var l=e.feed.entry[s].title.$t;l=l.substring(0,50);var o=e.feed.entry[s].media$thumbnail.url.replace(//s72-c-e100/,”/s260-e100″);o=o.replace(/http://1.bp.blogspot|http://2.bp.blogspot|http://3.bp.blogspot|http://4.bp.blogspot|https://2.bp.blogspot|https://3.bp.blogspot|https://4.bp.blogspot/,”https://1.bp.blogspot”),r+=’
‘+l+’…
“}r+=”http://thehackernews.com/”,document.getElementById(“result”).innerHTML=r}}),e=window,t=document,r=”script”,s=”stackSonar”,e.StackSonarObject=s,e[s]=e[s]”http://thehackernews.com/”function(){(e[s].q=e[s].q”http://thehackernews.com/”[]).push(arguments)},e[s].l=1*new Date,a=t.createElement(r),n=t.getElementsByTagName(r)[0],a.async=1,a.src=”https://www.stack-sonar.com/ping.js”,n.parentNode.insertBefore(a,n),stackSonar(“stack-connect”,”233″),o=!0)})});
//]]>




















Add Comment