Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
Category - Vulnerability Analysis
Vulnerability analysis, also known as vulnerability assessment, is a process that defines, identifies, and classifies the security holes (vulnerabilities) in a computer, network, or communications infrastructure.
Vulnerability scanner and information gatherer for the Concrete5 CMS. Is a little out of date presently pending a refactor. concrete5 is an open-source content...
XVNA is an extreme vulnerable node application coded in Nodejs(Expressjs)/MongoDB that helps security enthusiasts to learn application security. it’s not...
OWASP JoomScan (short for [Joom]la Vulnerability [Scan]ner) is an opensource project in perl programming language to detect Joomla...
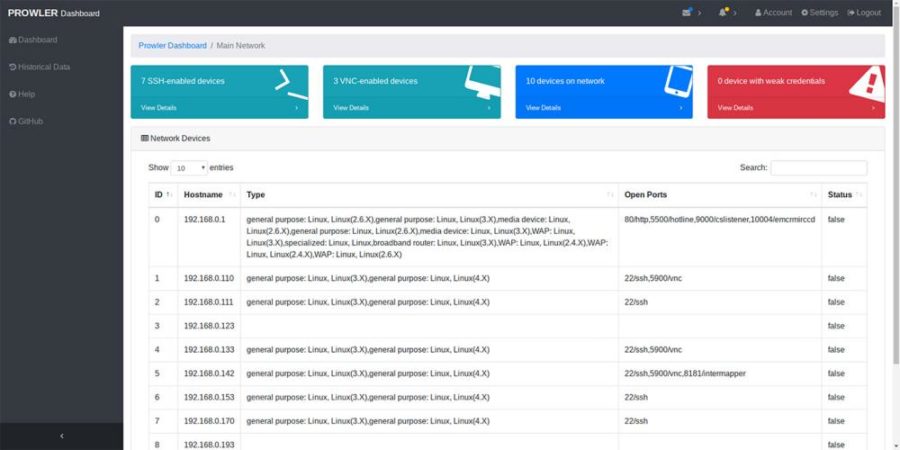
Prowler is a Network Vulnerability Scanner implemented on a Raspberry Pi Cluster, first developed during Singapore Infosec Community Hackathon – HackSmith v1.0...
Scanless is a command-line utility for using websites that can perform port scans on your behalf. Useful for early stages of a penetration test or if...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...
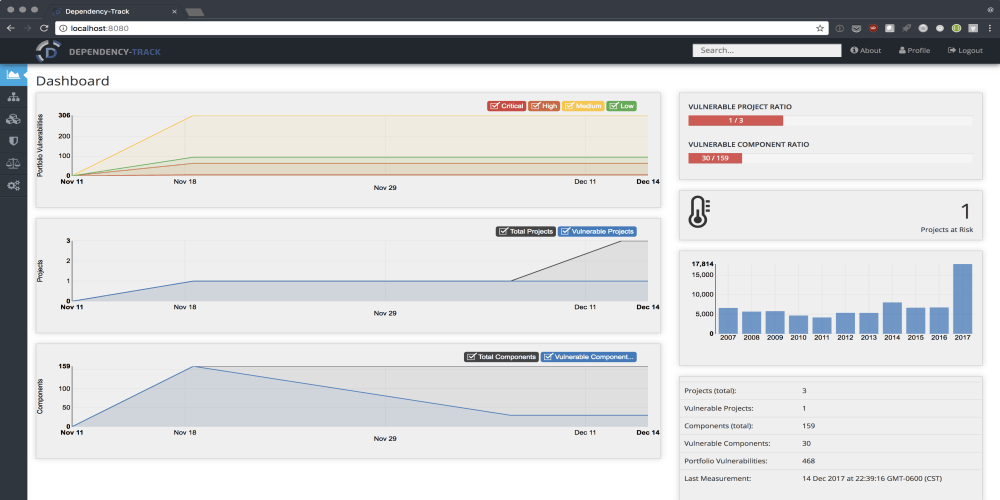
Modern applications leverage the availability of existing components for use as building blocks in application development. By using existing components...
Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) connected to the internet using a variety of...
Spectre & Meltdown Checker A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs...