The prosecutions were filed in California, Oregon, and Indiana, according to The News. The three incidents focus on the setback in Intel disclosing the...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
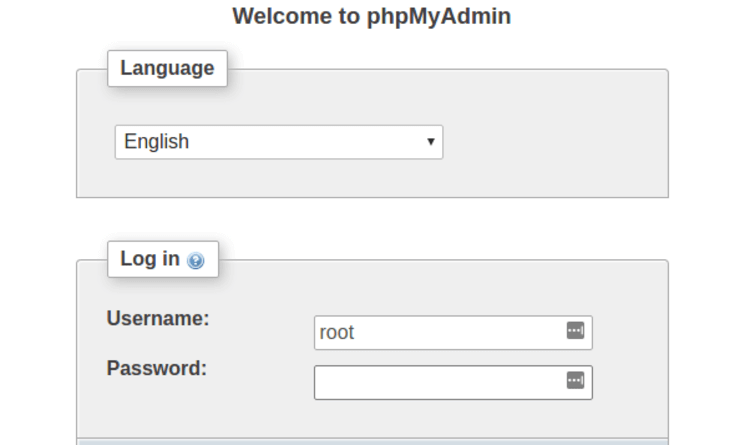
Amongst the most common and in demand applications for MySQL database management is the phpMyAdmin, which became vulnerable, when a critical flaw was found in...
The streaming company retweeted its care for the Internet Association’s Friday announced it would “interrupt in a judicial action to save net neutrality...
One of the biggest names in IT industry, Intel, has verified a report stating that some microprocessors have been built containing flaws in their design...
In today’s world, no company is fully safe as even big names like Sony and HBO have been hacked, and quite recently Nintendo’s Switch had to go through the...
Ben Wallace cited tech firms for staying happy to selling user data but not to give it to the administration which was being compelled to spend vast sums on de...
A security researcher (@s1guza) has published the details of an unpatched vulnerability in macOS that can be exploited to gain full control of a system. The...
A breach of Forever 21 left consumer payment card data exposed to hackers, the retailer verified Thursday. The business didn’t specify how many customers had...
Alphonso, a startup that retails media-viewing data, provides a plugin that listens for audio signals in shows and movies. Approximately 250 mobile...
Quite recently, the founder of Mcafee company, John Mcafee, was in news when his Twitter was hacked by an unknown hacker. This hacker used John’s social media...