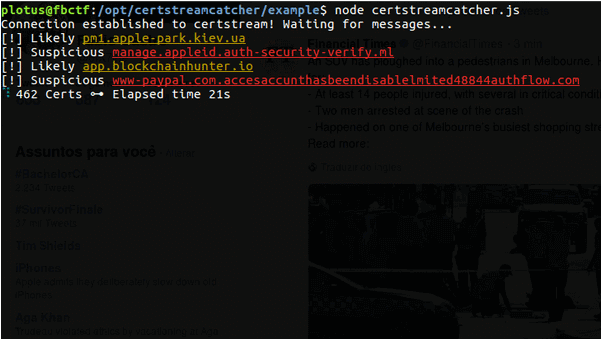
Catching phishing by observing certificate transparency logs. This tool is based on regex with effective standards for detecting phishing sites in real time...
Author - Mazen Elzanaty
A script for installing and automatically configuring DNSCrypt on Linux-based systems. Description DNSCrypt is a protocol for securing communications between a...
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
The corporation says that version 390 of its GPU video driver will be the last to carry 32-bit platforms. “Later driver release reports will not operate, nor...
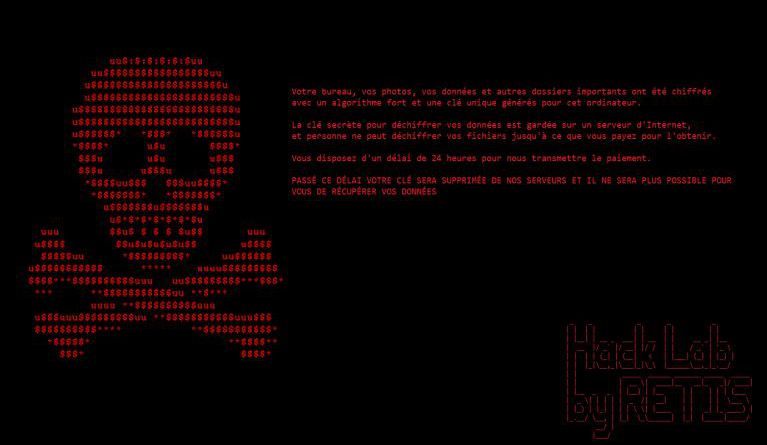
A security researcher has discovered a ransomware called Retis, which is a ransomware-type virus that secretly infiltrates the system. Shortly after executed...
Windows 10 Facial Recognition System Is Hackable According to some experienced cyber security researchers, it was revealed that the facial recognition system...
XAttacker is a Website Vulnerability Scanner & Auto Exploiter developed by Mohamed Riahi Auto Cms Detect [1] WordPress : [+] Adblock Blocker [+] WP All...
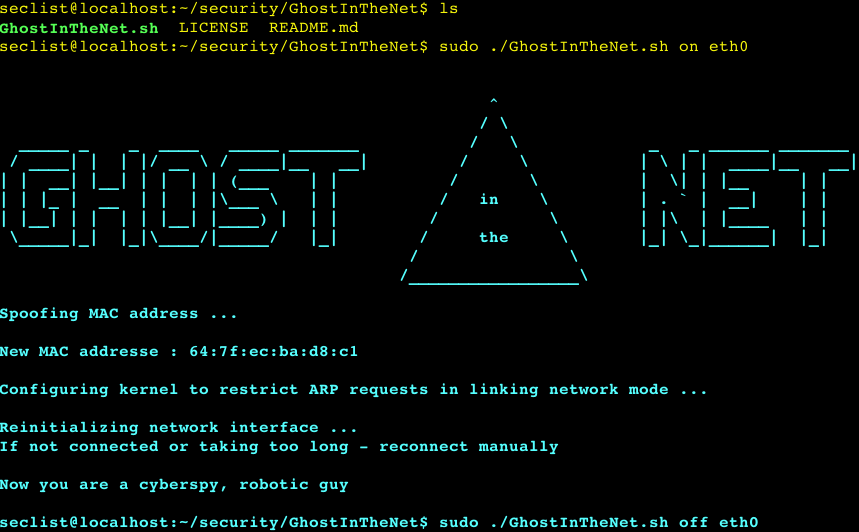
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
The macro_pack is a tool used to automatize obfuscation and generation of MS Office documents for pentest, demo, and social engineering assessments. The goal...
Invoke-MacroCreator is a powershell Cmdlet that allows for the creation of an MS-Word document embedding a VBA macro with various payload delivery and...