[sc name=”ad_1″]
A set of 36-year-old vulnerabilities has been uncovered in the Secure Copy Protocol (SCP) implementation of many client applications that can be exploited by malicious servers to overwrite arbitrary files in the SCP client target directory unauthorizedly.
Session Control Protocol (SCP), also known as secure copy, is a network protocol that allows users to securely transfer files between a local host and a remote host using RCP (Remote Copy Protocol) and SSH protocol.
In other terms, SCP, which dates back to 1983, is a secure version of RCP that uses authentication and encryption of SSH protocol to transfer files between a server and a client.
Discovered by Harry Sintonen, one of F-Secure’s Senior Security Consultants, the vulnerabilities exist due to poor validations performed by the SCP clients, which can be abused by malicious servers or man-in-the-middle (MiTM) attackers to drop or overwrite arbitrary files on the client’s system.
“Many scp clients fail to verify if the objects returned by the scp server match those it asked for. This issue dates back to 1983 and rcp, on which scp is based. A separate flaw in the client allows the target directory attributes to be changed arbitrarily. Finally, two vulnerabilities in clients may allow server to spoof the client output,” Sintonen explained.
In a specific attack scenario, an attacker-controlled server can drop .bash_aliases file to the victim’s home directory, which will trick the system into executing malicious commands within it as soon as the Linux user launches a new shell.
As explained by the researcher, “the transfer of extra files is hidden by sending ANSI control sequences via stderr.”
Multiple SCP Client Vulnerabilities
According to the advisory, the following-mentioned vulnerabilities were discovered in August last year, which were then responsibly reported to developers of vulnerable clients, including OpenSSH, PuTTY, and WinSCP.
- SCP client improper directory name validation (CVE-2018-20685)—a vulnerable scp client could allow a remote SCP server to modify permissions of the target directory by using empty (‘D0777 0 n’) or dot (‘D0777 0 .n’) directory name.
- SCP client missing received object name validation (CVE-2019-6111)—This vulnerability could allow a malicious SCP server to overwrite arbitrary files in the SCP client target directory. If a recursive operation (-r) is performed, the server can manipulate sub-directories as well (for example overwrite .ssh/authorized_keys).”
- SCP client spoofing via object name (CVE-2019-6109)—Due to missing character encoding in the progress display, the client output can be manipulated using ANSI code to hide additional files being transferred.
- SCP client spoofing via stderr (CVE-2019-6110)—This issue is also similar to the above one, allowing a malicious server to manipulate the client output.
Since the vulnerabilities impact the implementation of the SCP protocol, all SCP client applications, including OpenSSH, PuTTY, and WinSCP, which uses SCP as a standard to transfer files are affected.
WinSCP addressed the issues with the release of version 5.14 last October, and the patch is also included in the current version 5.14.4.
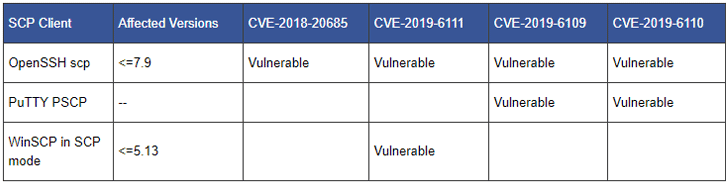
CVE-2018-20685 was patched in OpenSSH’s implementation of the SCP protocol in November, though the fix has not been formally released by the vendor yet. The rest three vulnerabilities remain unpatched in version 7.9, the latest version released in October.
However, if you are worried of malicious SCP server pwning you, you can configure your systems to use SFTP (Secure FTP) if possible.
Alternatively, Sintonen has also provided a fix to harden SCP against most server-side manipulation attempts, which you can apply directly, though it may cause some problems.
It seems like PuTTY has not fixed the vulnerabilities yet, since the last PuTTY release was version 0.7 in July 2017.
Users who think the vulnerabilities might impact them are recommended to keep an eye on the patches and apply them as soon as they become available for your client applications.




















Add Comment