Cryptocurrencies such as Bitcoin have been gaining more and more public attention over recent years. Now, the digital currency industry has hit Hollywood with...
Archive - July 2018
What is Cindicator? Cindicator fuses together machine learning and market analysis for asset management and financial analytics. The Cindicator team dubs this...
Hindsight is a free tool for analyzing web artifacts. It started with the browsing history of the Google Chrome web browser and has expanded to support other...
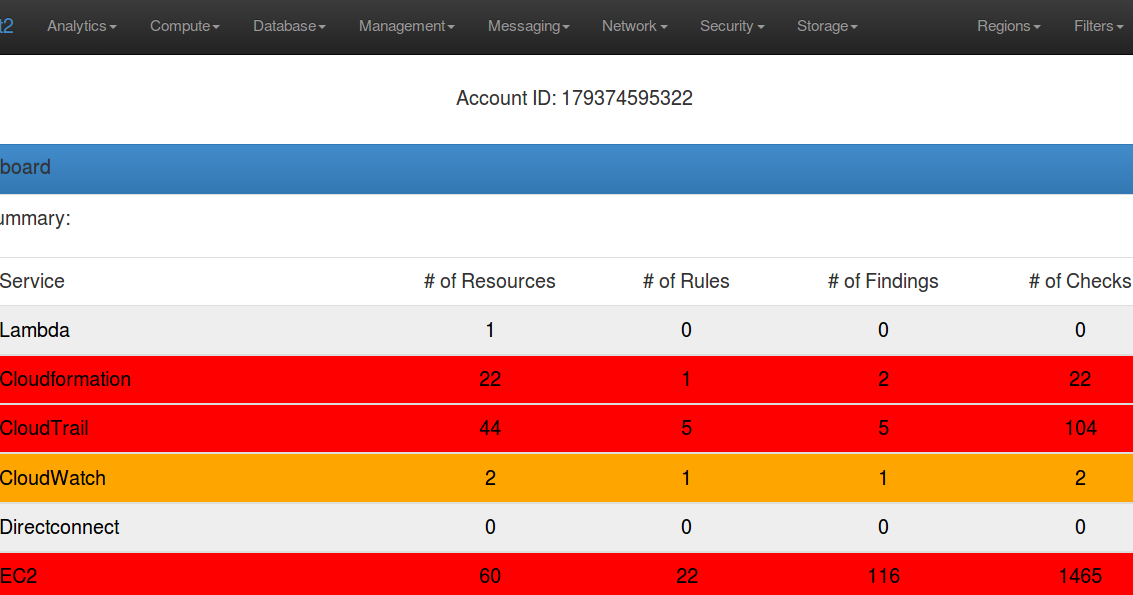
Scout2 is a security tool that lets AWS administrators assess their environment’s security posture. Using the AWS API, Scout2 gathers configuration data...
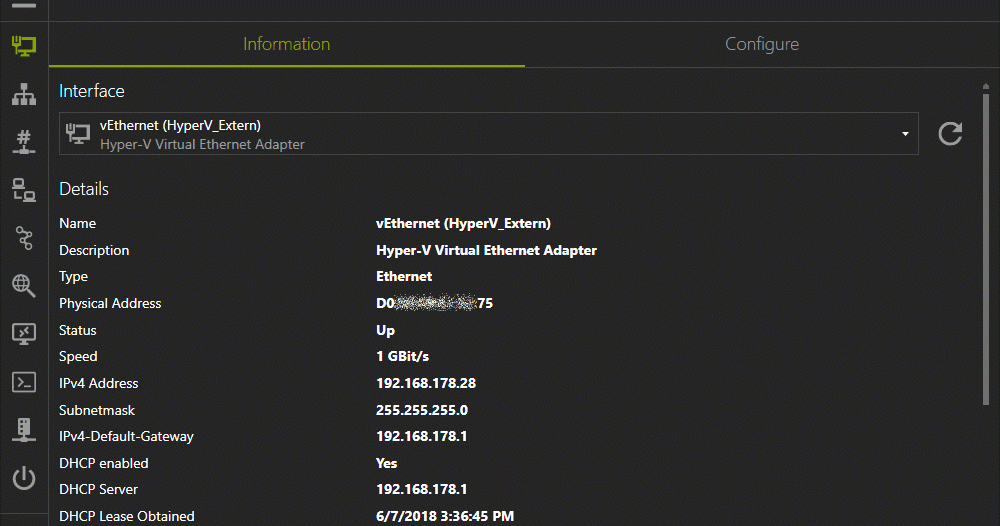
A powerful tool for managing networks and troubleshoot network problems! Features Network Interface – Information, Configure IP-Scanner Port-Scanner Ping...
Seeker utilizes HTML5, Javascript, JQuery and PHP to grab Device Information and GeoLocation with High Accuracy. Seeker Hosts a fake website on Apache Server...
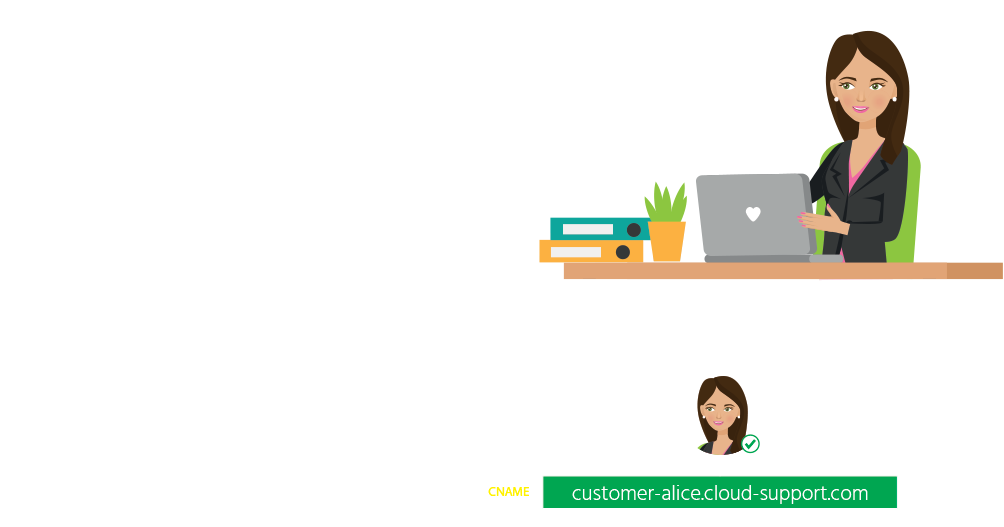
Domain Hijacking is a well-known security issue that can be carried in many different ways. In addition to social engineering or unauthorized access to the...
Security Monkey monitors your AWS and GCP accounts for policy changes and alerts on insecure configurations. Support is available for OpenStack public and...
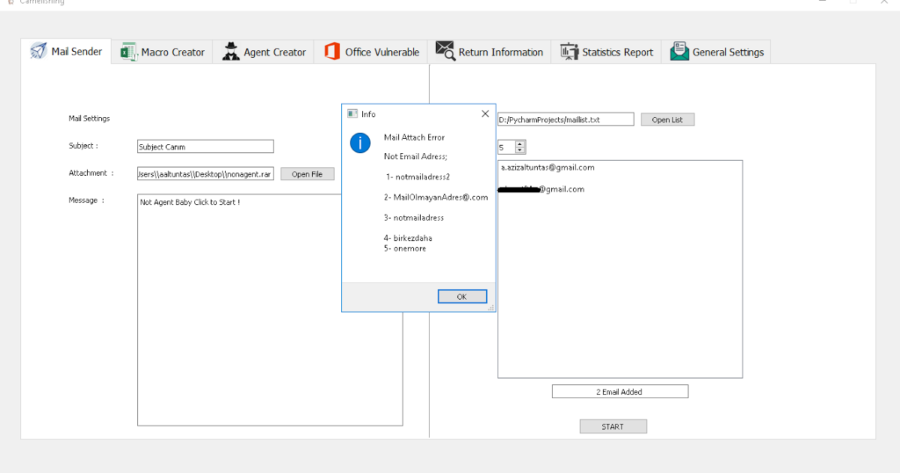
Camelishing Social Engineering Tool Features Bulk email sending Basic Python Agent Creator Office Excel Macro Creator DDE Excel Creator(or Custom Payload)...
Weevely is a web shell designed for post-exploitation purposes that can be extended over the network at runtime. Upload weevely PHP agent to a target web...