Another crop of Android apps hiding malware have been discovered in – and removed from – the Google Play store. Researchers at ESET discovered...
Tag - windows
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
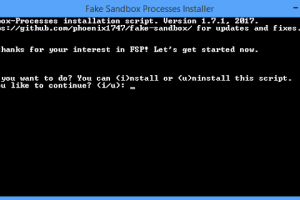
This small script will simulate fake processes of analysis, sandbox and/or VM software that some malware will try to avoid. You can download the original...
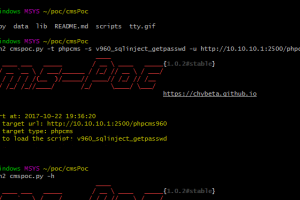
A CMS Exploit Framework. Requirements python2.7 Works on Linux, Windows Usage usage: cmspoc.py [-h] -t TYPE -s SCRIPT -u URL optional arguments: -h, --help...
Forever 21 is investigating a potential data breach which may have compromised customer information and payment cards. On Tuesday, the US clothing retailer...
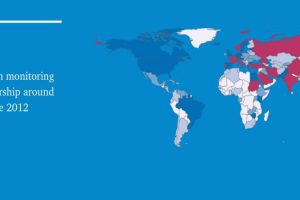
OONI, the Open Observatory of Network Interference, is a global observation network which aims is to collect high quality data using open methodologies, using...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
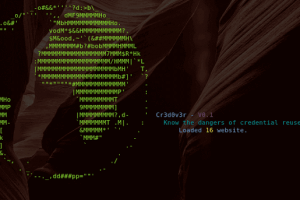
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
Faraday is the Integrated Multiuser Risk Environment you have always been looking for! It maps and leverages all the data you generate in real time, letting...
Mentalist is a graphical tool for custom wordlist generation. It utilizes common human paradigms for constructing passwords and can output the full wordlist as...