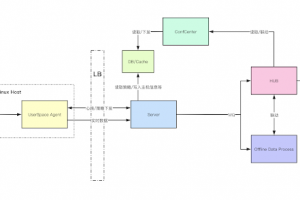
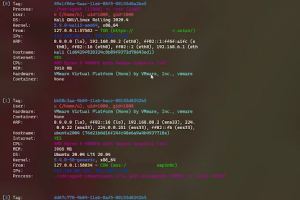
[sc name=”ad_1″] WordPress user enumeration and login Brute Force tool for Windows and Linux With the Brute Force tool, you can control how...
Tag - linux
[sc name=”ad_1″] CDK is an open-sourced container penetration toolkit, designed for offering stable exploitation in different slimmed containers...
[sc name=”ad_1″] ByteDance-HIDS is a Cloud-Native Host-Based Intrusion Detection solution project to provide next-generation Threat Detection and...
[sc name=”ad_1″] A pre-boot execution environment for Apple boards built on top of checkra1n. Building on macOS Install Xcode + command-line...
[sc name=”ad_1″] The all-in-one Red Team browser extension for Web Pentesters HackTools, is a web extension facilitating your web application...
[sc name=”ad_1″] This tool can be used to visualize the MUD files in JSON format. Motivation MUD files are plain text files in JSON format that...
[sc name=”ad_1″] linux post-exploitation framework made by linux user Still under active development 中文介绍 check my blog for updates how to use what...
[sc name=”ad_1″] SARENKA is an Open Source Intelligence (OSINT) tool which helps you obtaining and understanding Attack Surface. The main goal is...
[sc name=”ad_1″] drow is a command-line utility that is used to inject code and hook the entrypoint of ELF executables (post-build). It takes...
[sc name=”ad_1″] MaskPhish is a simple script to hide phishing URL under a normal looking URL(google.com or facebook.com). Legal Disclaimer: Usage...