[sc name=”ad_1″] Sherlock, a powerful command line tool provided by Sherlock Project, can be used to find usernames across many social networks. It...
Tag - kali linux tutorial
[sc name=”ad_1″] PhoneInfoga is one of the most advanced tools to scan international phone numbers using only free resources. The goal is to first...
Weevely is a web shell designed for post-exploitation purposes that can be extended over the network at runtime. Upload weevely PHP agent to a target web...
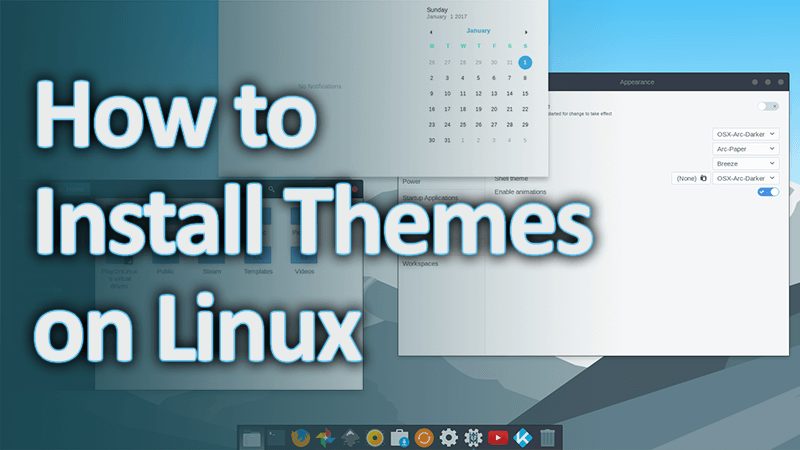
[sc name=”ad_1″] A theme is a collection of background image, window color and with theme can be given according to the picture as you wish. images...
pwnedOrNot is a python script which checks if the email account has been compromised in a data breach, if the email account is compromised it proceeds to find...
Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
The single most common causes of a broken Kali Linux installation are following unofficial advice, and particularly arbitrarily populating the system’s sources...
MAC Changer is an utility that makes the maniputation of MAC addresses of network interfaces easier. A media access control (Mac) address of a device is a...
Stacer is an open source system optimizer and Application Monitor that helps users to manage entire system with different aspects. The app will prompt you to...
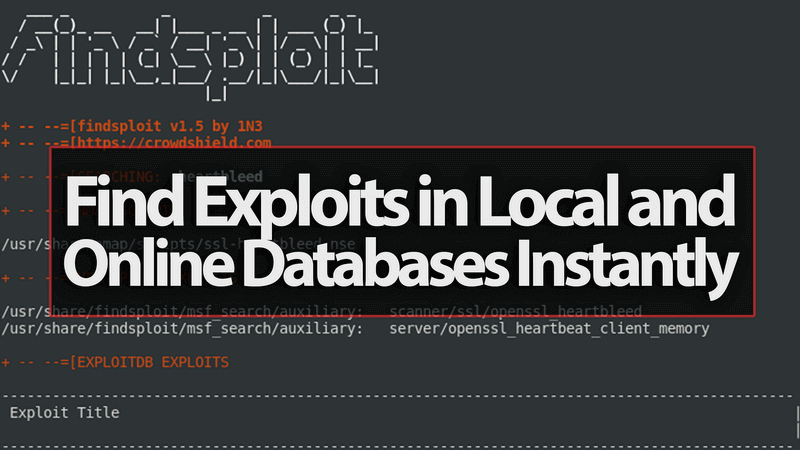
Findsploit is a simple bash script to quickly and easily search both local and online exploit databases. Findsploit: Installation: git clone cd Findsploit...