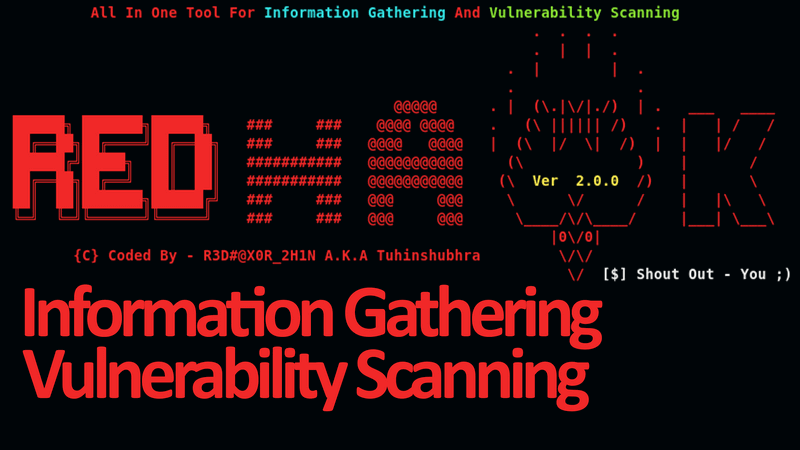
All in one tool for Information Gathering and Vulnerability Scanning RED HAWK : Scans That You Can Perform Using RED HAWK : Basic Scan Site Title NEW IP...
Tag - kali linux hacking tutorials
Mentalist is a graphical tool for custom wordlist generation. It utilizes common human paradigms for constructing passwords and can output the full wordlist as...
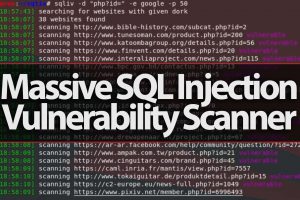
Hey Guys, In this video i show you a cool tool called SQLiv which used to scan websites for sql injection. SQLiv: Features: multiple domain scanning with SQL...
The official blog of jQuery—most popular JavaScript library used by millions of websites—has been hacked by some unknown hackers, using the pseudonym...
Bash script purposed for system enumeration, vulnerability identification and privilege escalation. MIDA Multitool draws functionality from several of my...
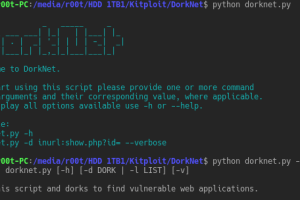
Selenium powered Python script to automate searching the web for vulnerable applications. DorkNet can take a single dork or a list of dorks as arguments. After...
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...
Multi-platform transparent client-side encryption of your files in the cloud. Cryptomator provides transparent, client-side encryption for your cloud. Protect...
CyberScan is an open source penetration testing tool that can analyse packets , decoding , scanning ports, pinging and geolocation of an IP including...
Programming Languages : BASH RUN root@ismailtasdelen:~# bash ./anti-ddos.sh Cloning an Existing Repository ( Clone with HTTPS ) git clone Cloning an Existing...