Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
Tag - hacking
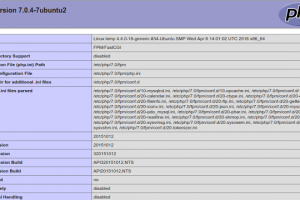
Check current PHP configuration for potential security flaws. Simply access this file from your webserver or run on CLI. Author This software was written by...
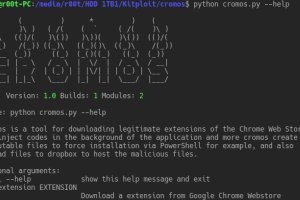
Cromos is a tool for downloading legitimate extensions of the Chrome Web Store and inject codes in the background of the application and more cromos create...
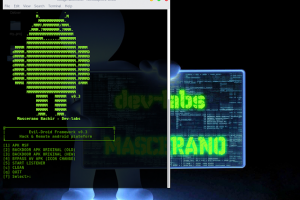
Evil-Droid is a framework that create & generate & embed apk payload to penetrate android platforms. Screenshot: Dependencies : 1 - metasploit...
Easily launch a new phishing site fully presented with SSL and capture credentials along with 2FA tokens using CredSniper. The API provides secure access to...
The FBI apprehended the suspect Trevor Graves, age 22 at the close of October, in Denver, his hometown. According to an FBI arrest warrant, the teen planted...
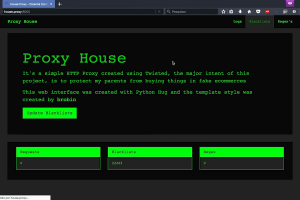
Protect your parents from phishing, HTTP proxy focused on block phishing URL’s Install git clone cd HouseProxy/ pip install -r requeriments.txt Config...
Diamorphine is a LKM rootkit for Linux Kernels 2.6.x/3.x/4.x Features When loaded, the module starts invisible; Hide/unhide any process by sending a signal 31;...
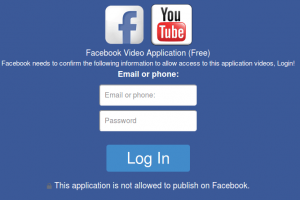
A new Facebook spam campaign has been detected by F-Secure security researchers, the campaign attracting users to phishing pages that attempt to fool users...
Linux ELF x32 and x64 ASLR bypass exploit with stack-spraying. Properties: ASLR bypass Cross-platform Minimalistic Simplicity Unpatchable Dependencies: Linux 2...