[sc name=”ad_1″] Paradoxia Remote Access Tool. Features Paradoxia Console Feature Description Easy to use Paradoxia is extremely easy to use, So...
Tag - Botnet
[sc name=”ad_1″] BSF provides a discrete simulation environment to implement and extend peer-to-peer botnets, tweak their settings and allow...
[sc name=”ad_1″] Aura Botnet C2 Server The botnet’s C2 server utilizes the Django framework as the backend. It is far from the most efficient...
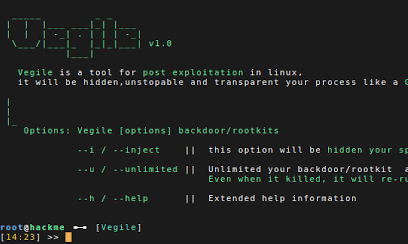
Vegile is a tool for Post exploitation Techniques in linux. Post Exploitation techniques will ensure that we maintain some level of access and can...
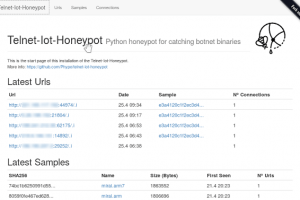
This project implements a python telnet server trying to act as a honeypot for IoT Malware which spreads over horribly insecure default passwords on telnet...
Just a year after Mirai—biggest IoT-based malware that caused vast Internet outages by launching massive DDoS attacks—completed its first anniversary, security...
A newly discovered unpatched attacking method that exploits a built-in feature of Microsoft Office is currently being used in various widespread malware attack...