StaCoAn is a crossplatform tool which aids developers, bugbounty hunters and ethical hackers performing static code analysis on mobile applications. This tool will look for interesting lines in the code which can contain:
- Hardcoded credentials
- API keys
- URL’s of API’s
- Decryption keys
- Major coding mistakes
This tool was created with a big focus on usability and graphical guidance in the user interface.
note that currently only apk files are supported, but ipa files will follow very shortly.
An example report can be found here: example report

Features
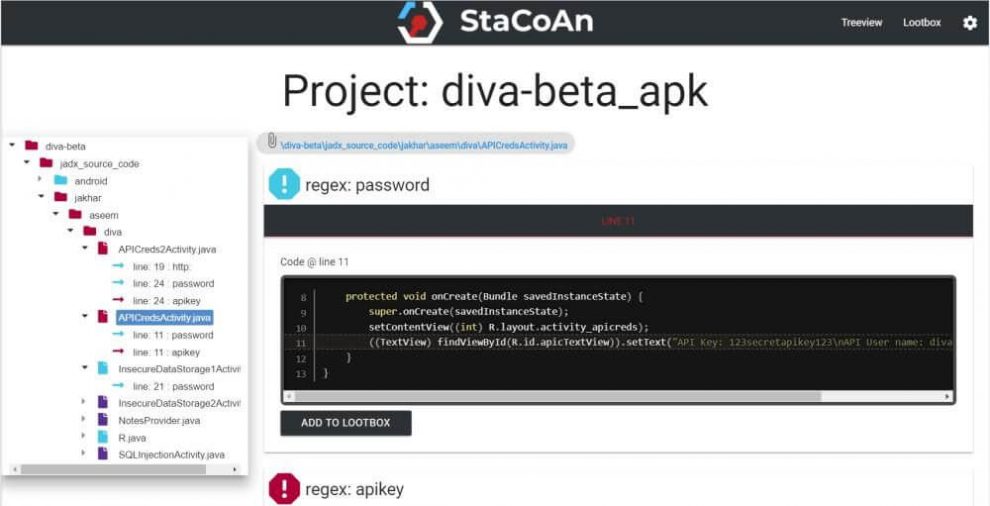
The concept is that you drag and drop your mobile application file (an .apk or .ipa file) on the StaCoAn application and it will generate a visual and portable report for you. You can tweak the settings and wordlists to get a customized experience.
The reports contain a handy tree viewer so you can easily browse trough your decompiled application.
Looting concept
The Loot Function let you ‘loot’ (~bookmark) the findings which are of value for you and on the loot-page you will get an overview of your ‘loot’ raid.
The final report can be exported to a zip file and shared with other people.
Wordlists
The application uses wordlists for finding interesting lines in the code. Wordlists are in the following format:
API_KEY|||80||| This contains an API key reference (https|http):\/\/.*api.*|||60||| This regex matches any URL containing 'api'
Note that these wordlists also support regex entries.
Limitations
This tool will have trouble with obfuscated code. If you are a developer try to compile without obfuscation turned on before running this tool. If you are on the offensive side, good luck bro.




















Add Comment