The administration of Guangzhou, center of the southern coastal province of Guangdong, began on Monday a pilot plan that creates a virtual ID card, which...
Search Results For - iOS
Los Angeles natives Stefan Bogdanovich and Dakota Speas, represented by Wilshire Law Firm, this firm honed a lawsuit with the U.S. District Court for the...
Wifiphisher is a security tool that mounts automated victim-customized phishing attacks against WiFi clients in order to obtain credentials or infect the...
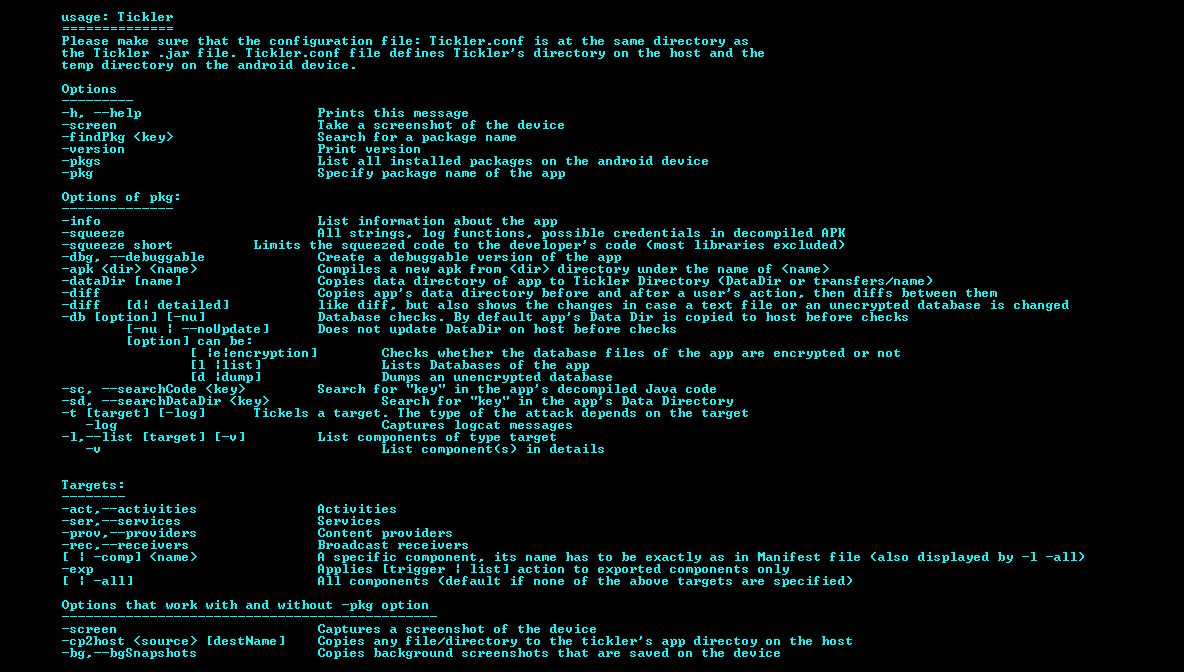
A java tool that helps to pentest Android apps faster, more easily and more efficiently. AndroTickler offers many features of information gathering, static and...
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
Apple is one of the biggest companies today, but its devices are not free from issues. Recently, it was reported that the company’s HomeKit software used to...
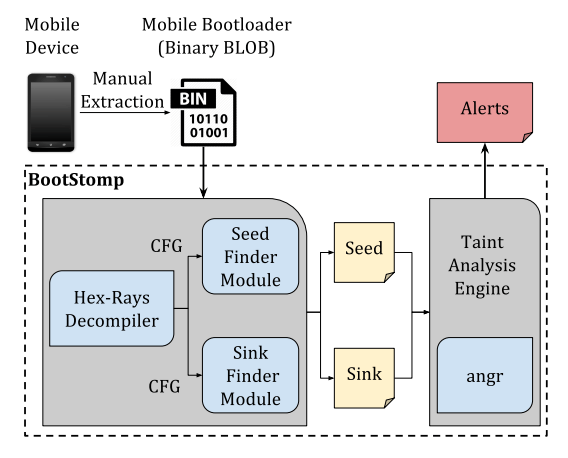
BootStomp is a boot-loader bug finder. It looks for two different class of bugs: memory corruption and state storage vulnerabilities. For more info please...
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
Adobe’s latest security update has swatted a total of 67 bugs, some of them critical, in Adobe Flash, Acrobat, and Reader. On Tuesday, the software...
Device drivers are an essential part in modern Unix-like systems to handle operations on physical devices, from hard disks and printers to digital cameras and...