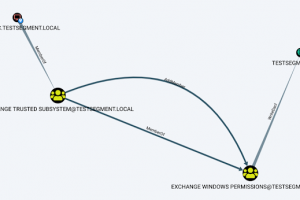
[sc name=”ad_1″] Aclpwn.py is a tool that interacts with BloodHound to identify and exploit ACL based privilege escalation paths. It takes a...
Search Results For - Windows
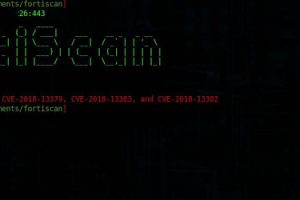
[sc name=”ad_1″] (CVE-2018-13379) Exploitation Tool, You can use this tool to check the vulnerability in your FortiGate SSL-VPN. ...
[sc name=”ad_1″] webscan is a browser-based network IP scanner and local IP detector. It detects IPs bound to the user/victim by listening on an...
[sc name=”ad_1″] An interactive command prompt that executes commands through proxychains and automatically logs them on a Cobalt Strike team...
[sc name=”ad_1″] Tool to manipulate and insert tracking pixels into Office Open XML documents. Features Insert tracking pixels into Office Open XML...
[sc name=”ad_1″] We at OpenEDR believe in creating a cybersecurity platform with its source code openly available to public, where products and...
[sc name=”ad_1″] Ping, but with a graph. Install FYI: The old Python version can be found under the python tag. Homebrew (MacOS + Linux) brew tap...
[sc name=”ad_1″] A cross-platform (Windows, Linux, Mac) hex editor for reverse engineering, and everything else. Features Large (1TB+) file support...
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] Linux evil toolkit is a framework that aims to centralize, standardize and simplify the use of various security tools for pentest...