[sc name=”ad_1″] This is a tool that allows you to offensively use YARA to apply a filter to the events being reported by windows event logging...
Search Results For - Windows
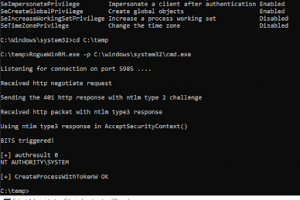
[sc name=”ad_1″] RogueWinRM is a local privilege escalation exploit that allows to escalate from a Service account (with SeImpersonatePrivilege) to...
[sc name=”ad_1″] Just a powershell scripts for auditing security with CIS BEST Practices Windows 10 and Window Server 2016 You just need to run the...
[sc name=”ad_1″] PYTMIPE (PYthon library for Token Manipulation and Impersonation for Privilege Escalation) is a Python 3 library for manipulating...
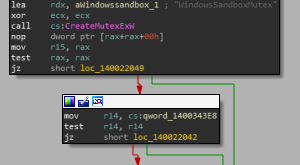
[sc name=”ad_1″] wsb-detect enables you to detect if you are running in Windows Sandbox (“WSB”). The sandbox is used by Windows...
[sc name=”ad_1″] Paradoxia Remote Access Tool. Features Paradoxia Console Feature Description Easy to use Paradoxia is extremely easy to use, So...
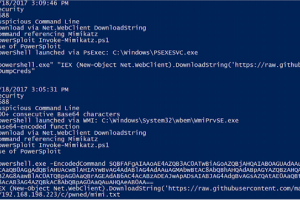
[sc name=”ad_1″] DeepBlueCLI – a PowerShell Module for Threat Hunting via Windows Event Logs Eric Conrad, Backshore Communications, LLC...
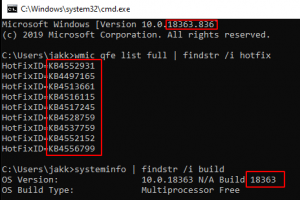
[sc name=”ad_1″] This is the code base for the service running on: . In short, PatchChecker is a web application (running on flask) that provides...
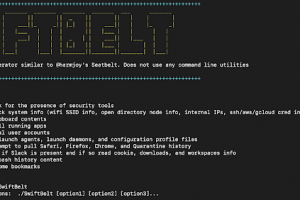
[sc name=”ad_1″] SwiftBelt is a macOS enumerator inspired by @harmjoy’s Windows-based Seatbelt enumeration tool. SwiftBelt does not utilize...
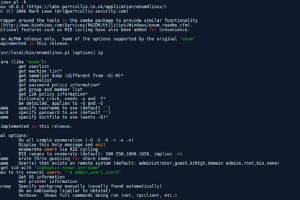
[sc name=”ad_1″] A Linux alternative to enum.exe for enumerating data from Windows and Samba hosts. Enum4linux is a tool for enumerating...